LPI Linux Certification in a Nutshell (30 page)
Read LPI Linux Certification in a Nutshell Online
Authors: Adam Haeder; Stephen Addison Schneiter; Bruno Gomes Pessanha; James Stanger
Tags: #Reference:Computers

Filesystem security is a fundamental requirement for any
multiuser operating system. The system’s files, such as the kernel,
configuration files, and programs, must be protected from accidents and
tampering by unauthorized people. Users’ files must be protected from
modification by other users and sometimes must be kept completely private.
In general, a form of
access control
must be
implemented to allow secure operations.
Native Linux filesystem access control is implemented
using a set of properties, maintained separately for each file. These
properties are collectively called the
access mode
, or simply the
mode
, of the file. The mode is a part of the file’s
inode, the information retained in the filesystem that describes the
file. A file’s mode controls access by these three classes of
users:
- User
The user who owns the file
- Group
The group that owns the file
- Other
All other users on the system
Like the mode, user and group ownership properties are a part of
the inode, and both are assigned when a file is created. Usually, the
owner is the user who created the file. The file’s group is usually set
to its creator’s default group. Group ownership adds flexibility in
situations in which a team shares files. The “other” users are those who
aren’t members of the file’s group and are not the file’s owner. For
each of these three user classes, the access mode defines three types of
permissions, which apply differently for files and directories. The
permissions are listed in
Table 7-2
.
Table 7-2. File permissions
Permission | Mnemonic | File permission | Directory permission |
|---|---|---|---|
Read | r | Examine the contents of the | List directory |
Write | w | Write to or change the | Create and remove files in the |
Execute | x | Run the file as a | Access ( |
These three permissions apply to the three different
classes of users:
user, group
, and
other
. Each has
read,
write
, and
execute
permissions, as shown in
Figure 7-1
.
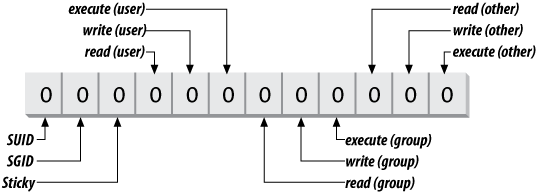
Figure 7-1. Access mode bits
All of the permissions are binary (either granted or not granted)
and are thought of as single binary bits in the access mode. When
displayed by commands such as
ls
, the permissions
use the mnemonic in
Table 7-2
for the true
state and a hyphen for the false state. To represent only the read
permission, for example,r--would be
used. Read and execute together, typical for directories, would be
denotedr-x. These notations are
usually offered in sets of three, such as:
rw-rw-r--
A file with this setting would give read/write permission to the
user and group, and read-only permission to everyone else.
In addition to the nine bits for user, group, and other, the
access mode contains three more bits, which control special attributes
for executable files and directories:
- SUID
The SUID property is for executable files only and
has no effect on directories. Normally the user who launches a
program owns the resulting process. However, if an executable file
has its SUID bit set, the file’s owner owns the resulting process,
no matter who launched it. When SUID is used, the file’s owner is
usually root. This offers anyone temporary root access for the
duration of the command. An example of an SUID program is
passwd
. This command needs special access to
manipulate the shadow password file
(
/etc/shadow
), and runs as user
root
.Using the SUID bit in cases like
passwd
enhances security by allowing access to secure functions without
giving away the root password. On the other hand, SUID can be a
security risk if access is granted unwisely. For example, consider
a situation where
/bin/vi
was set to SUID
mode. Any user would be able to edit any file on the
system!- SGID
The SGID property works the same way as SUID for
executable files, setting the process group owner to the file’s
group. In addition, the SGID property has a special effect on
directories. When SGID is set on a directory, new files created
within that directory are assigned the same group ownership as the
directory itself. For example, if directory
/home/fin
has the group
finance
and has SGID enabled, then all files
under
/home/fin
are created with group
ownership of
finance
, regardless of the
creator’s group. This is an important attribute for teams,
ensuring that shared files all have the same group
ownership.- Sticky
At one time, the
sticky bit
applied to
executable programs, flagging the system to keep an image of the
program in memory after the program finished running. This
capability increased performance for subsequent uses by
eliminating the programs’ load phase, and was applied to programs
that were large or were run frequently. Modern virtual memory
techniques have made this use unnecessary, and under Linux there
is no need to use the sticky bit on executable programs.When applied to a directory, the sticky bit offers
additional security for files within the directory. Regardless of
file permissions, the only users who can rename or delete the
files from a directory with the sticky bit set are the file owner,
the directory owner, and
root
. When used in a
team environment, the sticky bit allows groups to create and
modify files but allows only file owners the privilege of deleting
or renaming them. The
/tmp
directory on Linux
systems usually has the sticky bit set, to allow any user to write
to it, but allow only the file owner to delete files or
directories.
Like the other access controls, these special properties are
binary and are considered bits in the access mode.
The
special, user, group
, and
other
permissions can be represented in a string
of 12 binary bits, as shown in
Figure 7-2
.
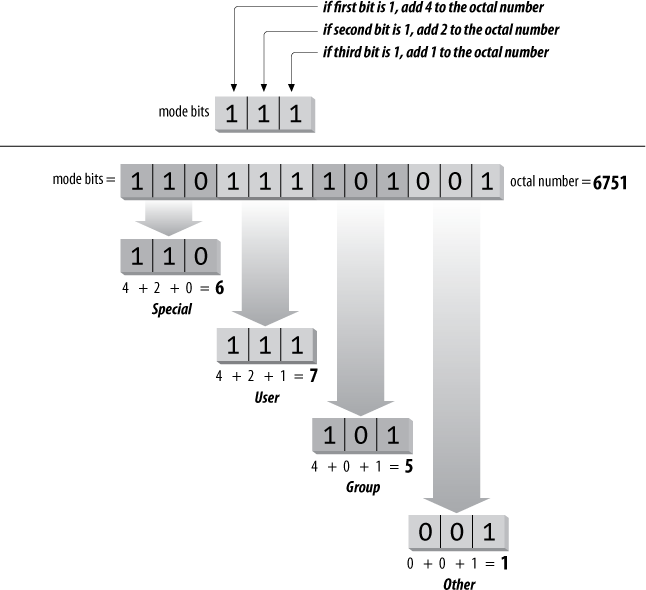
Figure 7-2. Changing permission bits to an octal number
It is common to refer to these bits in four sets of three,
translated into four octal (base-8) digits. The first octal digit
represents the
special permissions SUID, SGID, and sticky. The other
three represent the read, write, and execute permissions,
respectively, in each of the user, group, and other user classes.
Octal notation is used as shorthand for binary strings
such as the access mode, and each group of three bits has
2
3
= 8 possible values, listed in
Table 7-3
.
The read permission by itself isr--, which can be thought of as binary 100,
or octal 4. Adding the write permission yieldsrw-, or binary 110, which is octal 6.
Figure 7-2
shows how to
total bit values into the octal equivalents. Memorizing, or even
writing, the binary-to-octal equivalents may be easier on the exam
than adding bit values. Use the technique that works best for
you.
Table 7-3. Octal numbers
Octal value | Binary equivalent |
|---|---|
0 | 000 |
1 | 001 |
2 | 010 |
3 | 011 |
4 | 100 |
5 | 101 |
6 | 110 |
7 | 111 |
To turn the mode bits110111101001into an octal representation,
first separate them into chunks of three bits:110, 111, 101, and001. The first group, representing the
special permissions, is110. This can be thought of as 4 + 2 + 0 =
6. The second group, representing user permissions, is111, or 4 + 2 + 1 = 7. The third group,
representing group permissions, is101, or 4 + 0 + 1 = 5. The last group,
representing other permissions, is001, or 0 + 0 + 1 = 1. The mode string for
this example can then be written as the octal 6751.
This is the form used to display the file mode in the output
from the
stat
command. Here, the octal access
mode for the
mount
command is 4755:
#stat /bin/mountFile: `/bin/mount'
Size: 69100 Blocks: 144 IO Block: 4096 regular file
Device: fd00h/64768d Inode: 14671934 Links: 1
Access: (4755/-rwsr-xr-x) Uid: ( 0/ root) Gid: ( 0/ root)
Access: 2009-08-07 15:40:29.000000000 -0500
Modify: 2009-06-01 06:17:46.000000000 -0500
Change: 2009-06-29 14:37:58.000000000 -0500
The special permissions are represented in this example by octal
4, or binary 100, indicating that the SUID permission is set (-rws). The user permission is octal 7, or
binary 111, indicating read, write, and execute for the file’s owner
(in this case,
root
). Both the group and other
permissions are set to octal 5, or binary 101, indicating read and
execute, but not write.
As mentioned earlier, the user, group, and other
permissions are often spelled out in symbolic mode descriptions such
asrwxr-xr-x. This notation is
found in the output of the
ls -l
and
stat
commands. As you can see in the access mode
for
mount
, this scheme is modified slightly in
the presence of special permissions. Instead of adding three more bits
to the left ofrwxr-xr-x, the SUID
permission is indicated in the string by changing the user execute
position fromxtos. SGID permission is handled the same way.
The sticky permission is indicated by replacingxin the other execute position withT. For example, an executable
program with mode 6755 would have the following equivalent symbolic
mode:
rwsr-sr-x
A directory with mode 1774 would have this equivalent
string:
rwxr-xr-T
While this layering of special permissions may appear to obscure
the underlying execute permissions, it makes sense. The special
permissions are relatively rare in the filesystem, so depicting the
three extra bits would waste space on your terminal or terminal
window. When the executable bits are set, the setuid and setgid bits
are represented withs. When the
executable bits are not set, the setuid and setgid bits are
represented withS. Similarly, the
sticky bit is represented with eithertorT.
