Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers
Reverse Deception: Organized Cyber Threat Counter-Exploitation (115 page)

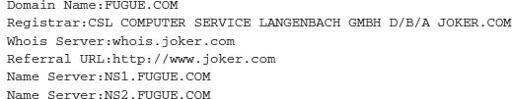
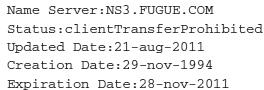
This information illustrates that the domain itself has been registered for quite some time and is currently set to expire on 11/28/2011. We can see that the domain has been registered for a while via a German registrar, and is registered to a citizen in the United States and an IP address in the United States hosted by the Internet Systems Consortium. This requires us to dig a little deeper as to why a bot agent would want to check connectivity to a well-established server.
Now look at the next UDP stream generated by this executable, which is similar to a connectivity check for the crimeware agent:
Here is another example of the sample simply attempting to connect to a well-known IP address that is not an actual IP address, but a predetermined or expected response is the goal. This information was gleaned from less than five minutes of running the executable within a sandbox. Imagine if we ran this longer.
With this information, we can determine there is level of sophistication by using well-known servers to check connectivity, although this is more widely used today than most professionals think. The observable patterns from this can be seen as connections to
fugue.com
and the well-known IP address and port of 239.255.255.250, which should be enough to quickly identify other systems that may be infected by this operator.
If the systems that are connecting are Linux-based systems, you may not need to worry, as this infection is a Win32-based executable. However, the Linux-based systems could be propagating the Win32 malware to Windows-based systems.
Example: MD5 of 70cb444bf78da9c8ecf029639e0fb199
The following sample is a little more sophisticated than the previous one, and has been designed to perform additional actions that enable more stealthy and persistent functions:
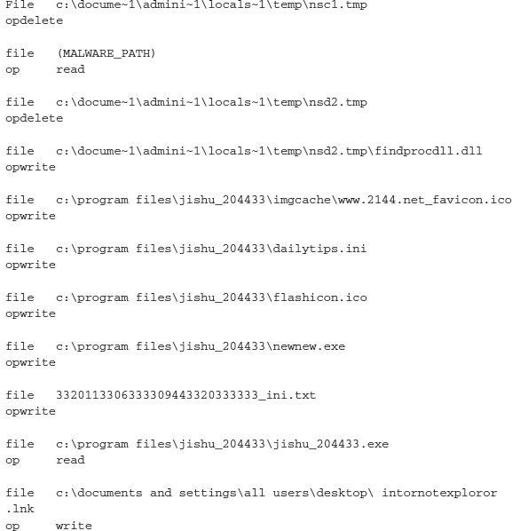
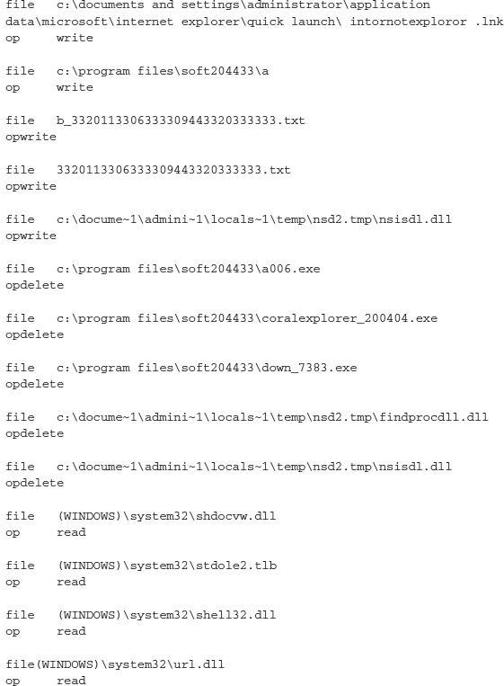
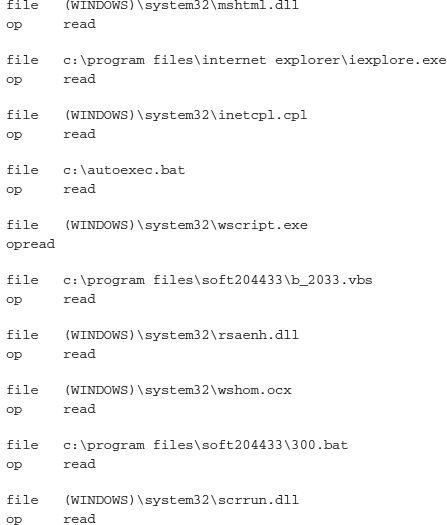
After performing actions on a host, this sample executes the following process:
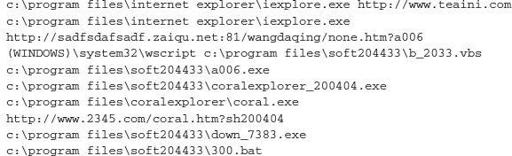
As you can see, this crimeware campaign is much more active than the previous example. It has numerous callback functions to a remote server upon initial infection, and updates itself upon exploitation and installation. This level of detail can help an analyst better understand what a malicious sample is doing
There are numerous paths in which the executable will read and write to files. However, there is an observable pattern that can be used for host-based detection. The primary paths you would want to look at are \locals~1\temp\, program files\jishu_204433\, \documents and settings\all users\desktop\, and :\program files\soft204433\.
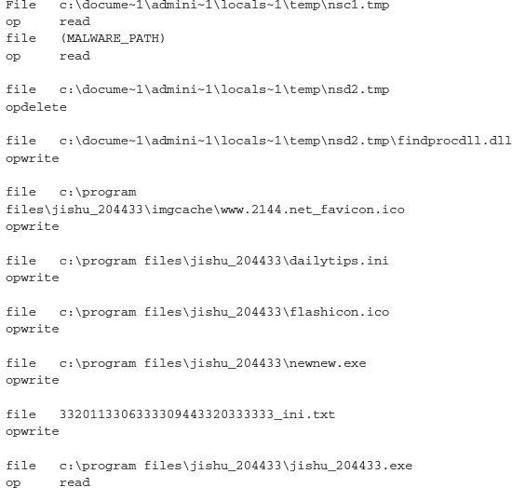
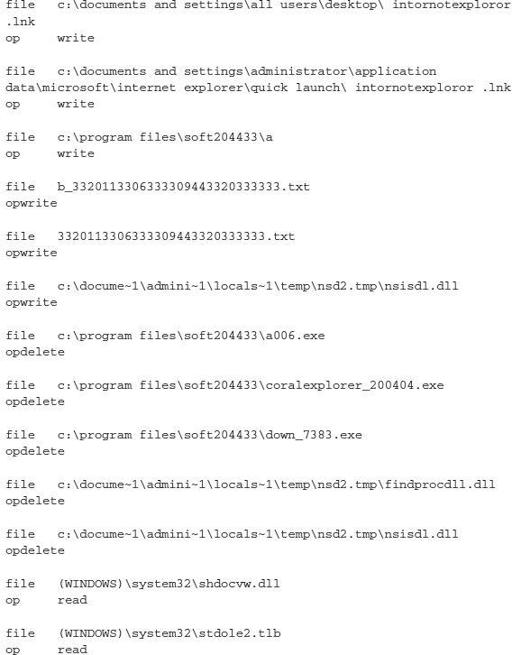
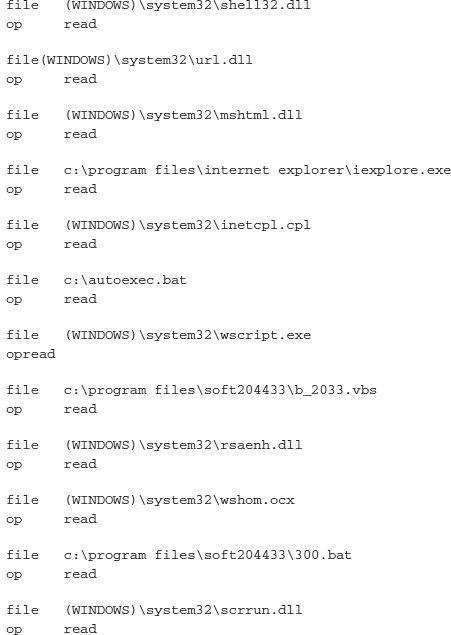
Again, there is a unique pattern to this executable’s host-based intentions. By reading numerous DLLs, you can gather some information that will help you determine what the capabilities of the crimeware may be.
Now that we have taken a moment to review the host-based activity, let’s look at some of the network activities of this executable.
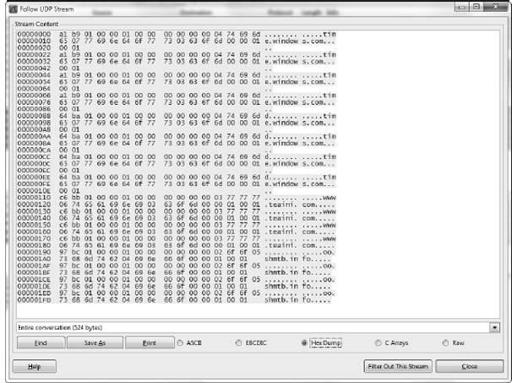
This executable not only attempts to check with
time.windows.com
, but also tries to connect to two other domains:
www.teaini.com
and
oo.shmtb.info
, which are both associated with an IRC bot-based virus or threat that has been recorded in public blacklists dating back to May 2011.

