Reverse Deception: Organized Cyber Threat Counter-Exploitation (66 page)
Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers

The Swiss, being keenly prepared for this possibility, relied on a team of specialists to swing the advantage in their favor. They knew that the Germans were purchasing more sophisticated technologies in preparation for future battles. Several years earlier, a few human intelligence specialists from the Swiss military had contacted the foreign subcontractor under Paul and Rick’s corporation who specialized in creating the German software slated to provide the real-time data for tracking forces. After much research into the lives of several contractors at this facility, the Swiss identified a couple of personnel sympathetic to their cause. These individuals, armed with several new lines of code developed by the Swiss, created additional functionality in the German tracking system, which the Germans would never know about … until it was too late.
When the Germans started making their way across the Swiss border, the Swiss computer specialists’ work began. Back at the main German headquarters, where the brass was observing the real-time movements of their forces, their display began to show German forces dispersing in a manner inconsistent with their operational plan. This same information was displayed on the fighting units’ displays, on which the German forces had become so reliant. As the chatter increased among the Germans to return to their predetermined formations, heated arguments ensued that all forces were in place as had been planned. This served as a useful distraction for the Swiss.
The extra lines of code provided by the Swiss allowed them access to the German tracking system. With this access, the Swiss specialists were able to view the exact locations of the German forces, as well as tamper with the displays and force locations as seen by the Germans. With the Germans confused about their own locations, and the Swiss having full knowledge of the German locations, the Swiss unleashed an assault that drove the Germans back across the border posthaste. With a little research, well-placed contacts, and technical skills, the Swiss had preserved the sanctity of their homeland with minimal loss of their fighting forces.
Postmortem
One overlooked aspect of information security involves acquisition security. Secure contracting and acquisition channels are often taken for granted. A secure acquisition channel does not guarantee a secure acquisition, and the same goes for secure contracting: it is not a guarantee. The factors involved in assessing acquisition and contracting are not all inclusive, but they are as comprehensive as reasonably possible. An additional look at these processes and programs should be a part of every security professional’s routine.
Technology giveth and technology taketh away, and not always in equal measure
.
—Neil Postman, “Informing Ourselves to Death” (speech at the German Informatics Society meeting, October 1990)
The prospect of coordinated and complex virtual deception is a reality. To improve security, paradigms must be broken, and new ideas must be incorporated and synchronized with traditional efforts. The linear thinking that leads us down the path of compliance with security recommendations of industry and government leaves us inherently vulnerable. Both attacker and defender share knowledge of every aspect of the network. Governments give us standards that are published for the world to see. It must be done that way for compliance. Industries develop their products, which they sell, so advertising and specifications are out there for both the attacker and defender. Unwittingly, the defenders lose the traditional home-field advantage because the attackers already know with what and how the defenders are doing their job; game over.
In recent years, military actions have been prefaced with deception and cyber attacks. It is believed Russia launched attacks on two occasions: one against Estonia and a second against Georgia. Both times, it crippled critical infrastructure and staggered the IT security folks. With Symantec commercializing its honeypots, an additional level of obfuscation for attackers and defenders alike has been added to the mix. How will this play out with the commercial sector engaging in military-style tactics to defend its networks?
Traditional honeypots are used for early warning and surveillance, but in the nonlinear asymmetric world, should more be done with them? By definition, honeypots should have no production value, and everything that touches them is malware and nefarious. But should that be the limit? Along with software and networking issues, computers have inherent structural vulnerabilities, as there are regular vulnerabilities introduced into various platforms by vendors.

Tall Tale 4
A senior-ranking executive of an international organization (let’s call him Mr. Smith) was sent an e-mail regarding a 20-year college reunion. He was aware that it was his upcoming 20th-year reunion, so he read the sender’s address, the subject, and the body of the e-mail. After feeling somewhat comfortable with the e-mail’s content, he looked at its attachments, which were said to be an RSVP form in Microsoft Word format and a flyer for the reunion in PowerPoint format. He opened the attachments without a second thought, and then after reading them, he realized something was wrong because the content for the attachments was slightly off. One of the images was used in the last reunion according to his memories of the previous event.
Mr. Smith called a colleague he had graduated with, and discovered that peer had not received anything. That old classmate had knowledge of the real reunion, and told Mr. Smith that the date and location of the upcoming reunion were all wrong, and the coordinators on the RSVP form were also incorrect. This sent an immediate red flag, and the hairs on the back of Mr. Smith’s neck went up. Working for an organization that handles sensitive projects for the government, he knew of the dangers of spear phishing and SSCTs.
Mr. Smith then called his security manager to send a trusted team of digital forensic investigators to his office and inspect his computer for any possible foul play. As he waited for the investigators to arrive, he began to sweat as he considered the volume of sensitive information he had stored on his laptop and all of the critical information that could be lost if this were an incident. Some time passed before the team arrived in Mr. Smith’s office and began examining his laptop for any possible infections. They performed the standard operating procedures, by first disconnecting the system from the enterprise’s network and then making copies of his Microsoft Outlook e-mail file folders where a possible infection may be residing. The team told Mr. Smith they did not want to turn off his system, but wanted to leave it unplugged for the time being in the event there was an infection present and it was memory-resident. If the system were turned off, they might lose additional evidence if the initial exploit code in the attachments had already downloaded the stage-two sample from a remote site. They didn’t want to take the chance of losing any information if something had occurred. From that point on, all information between the infected system and the remote connections were logged for analysis.
The security team headed away with a copy of Mr. Smith’s Outlook files and folders on a flash drive and his laptop still running (and power supply in tow). Luckily, this organization had a proactive policy of making a backup image of every senior-ranking official’s laptop and had a four-month-old image of Mr. Smith’s laptop. The examiners copied Mr. Smith’s Outlook files and folders to the appropriate location on his backup Windows system, which they were running within a virtual machine (VM) based on the Linux platform’s Xen Virtual Machine Manager (VMM) environment. While this task was being carried out, another investigator plugged Mr. Smith’s laptop into a sandboxed network running the same DHCP range as the corporate network. This provided perceptual consistency to network-aware malware, which can shut down if plugged into networks not associated with specific network ranges. With both systems being set up together on two separate sandboxes, and network sniffers running on each network, both systems were monitored for a planned period of 24 hours. For the purpose of this tall tale, we are going to call the VM system Honeypot 1 and the system being investigated System A.
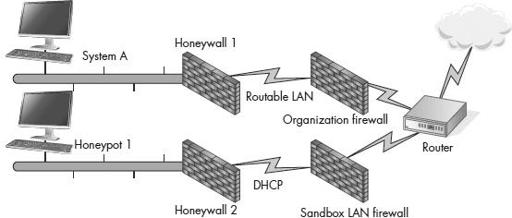
A counterintelligence operations network
Honeypot 1
An interesting thing occurred when the examiners installed the suspicious Outlook files, opened Mr. Smith’s e-mail, and followed the same path that Mr. Smith had told them he had taken when opening the message and the attachments. Once the attachments were opened, a process had opened a TCP socket and began phoning out (communicating with a remote system) to
www.hotgirltvshow.com
, and attempted some HTTP POST and GET commands. Luckily, this sandbox actually had an Internet connection and was able to download the stage-two Trojan, which came right down in both an executable (.exe) and a dynamic link library (DLL) file. Once these files were on the system, using external analysis tools for VM introspection (tools that can inspect the functions and actions of a VM), the team was able to ascertain the executed commands of the stage-two Trojan that had been downloaded from
www.hotgirltvshow.com
. The following commands were initially executed on the system (in this order):
putfile:
door:
findpass2000
