Windows Server 2008 R2 Unleashed (146 page)
Read Windows Server 2008 R2 Unleashed Online
Authors: Noel Morimoto

four primary execution policies, discussed in more detail in the following sections:
Restricted, AllSigned, RemoteSigned, and Unrestricted.
NOTE
Execution policies can be circumvented by a user who manually executes commands
found in a script file. Therefore, execution policies are not meant to replace a security
system that restricts a user’s actions and instead should be viewed as a restriction
that attempts to prevent malicious code from being executed.
Restricted
By default, PowerShell is configured to run under the Restricted execution
policy. This execution policy is the most secure because it allows PowerShell to operate
only in an interactive mode. This means no scripts can be run, and only configuration
files digitally signed by a trusted publisher are allowed to run or load.
AllSigned
The AllSigned execution policy is a notch under Restricted. When this policy is
enabled, only scripts or configuration files that are digitally signed by a publisher you
730
CHAPTER 21
Automating Tasks Using PowerShell Scripting
trust can be run or loaded. Here’s an example of what you might see if the AllSigned
policy has been enabled:
PS C:\Scripts> .\evilscript.ps1
The file C:\Scripts\evilscript.ps1 cannot be loaded. The file
C:\Scripts\evilscript.ps1 is not digitally signed. The script will not
execute on the system. Please see “get-help about_signing” for more
details.
At line:1 char:16
+ .\evilscript.ps1 <<<<
PS C:\Scripts>
Signing a script or configuration file requires a code-signing certificate. This certificate can
come from a trusted certificate authority (CA), or you can generate one with the
Certificate Creation Tool (Makecert.exe). Usually, however, you want a valid code-signing
certificate from a well-known trusted CA, such as VeriSign, Thawte, or your corporation’s
internal Public Key Infrastructure (PKI). Otherwise, sharing your scripts or configuration
files with others might be difficult because your computer isn’t a trusted CA by default.
RemoteSigned
The RemoteSigned execution policy is designed to prevent remote
ptg
PowerShell scripts and configuration files that aren’t digitally signed by a trusted publisher
from running or loading automatically. Scripts and configuration files that are locally
created can be loaded and run without being digitally signed, however.
A remote script or configuration file can be obtained from a communication application,
such as Microsoft Outlook, Internet Explorer, Outlook Express, or Windows Messenger.
Running or loading a file downloaded from any of these applications results in the follow-
ing error message:
PS C:\Scripts> .\interscript.ps1
The file C:\Scripts\interscript.ps1 cannot be loaded. The file
C:\Scripts\interscript.ps1 is not digitally signed. The script will not execute on
the system. Please see “get-help about_signing” for more details..
At line:1 char:17
+ .\interscript.ps1 <<<<
PS C:\Scripts>
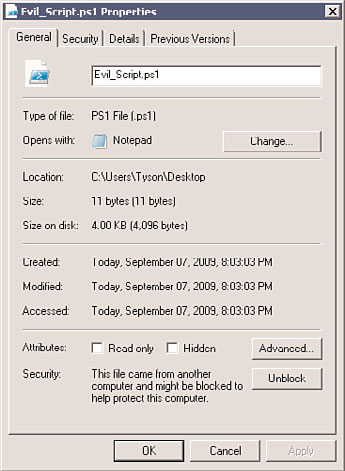
To run or load an unsigned remote script or configuration file, you must specify whether
to trust the file. To do this, right-click the file in Windows Explorer and click Properties.
On the General tab, click the Unblock button (see Figure 21.2).
After you trust the file, the script or configuration file can be run or loaded. If it’s digitally
signed but the publisher isn’t trusted, however, PowerShell displays the following prompt:
PS C:\Scripts> .\signed.ps1
Do you want to run software from this untrusted publisher?
Understanding the PowerShell Basics
731
21
ptg
FIGURE 21.2
Trusting a remote script or configuration file.
File C:\Scripts\signed.ps1 is published by CN=companyabc.com, OU=IT,
O=companyabc.com, L=Oakland, S=California, C=US and is not trusted on your
system. Only run scripts from trusted publishers.
[V] Never run [D] Do not run [R] Run once [A] Always run [?] Help
(default is “D”):
In this case, you must choose whether to trust the file content.
Unrestricted
As the name suggests, the Unrestricted execution policy removes almost all
restrictions for running scripts or loading configuration files. All local or signed trusted
files can run or load, but for remote files, PowerShell prompts you to choose an option for
running or loading that file, as shown here:
PS C:\Scripts> .\remotescript.ps1
Security Warning
Run only scripts that you trust. While scripts from the Internet can be useful,
this script can potentially harm your computer. Do you want to run
C:\Scripts\remotescript.ps1?
[D] Do not run [R] Run once [S] Suspend [?] Help (default is “D”):
In addition to the primary execution policies, two new execution policies were introduced
in PowerShell 2.0, as discussed in the following sections.
732
CHAPTER 21
Automating Tasks Using PowerShell Scripting
Bypass
When this execution policy is used, nothing is blocked and there is no warning or
prompts. This execution policy is typically used when PowerShell is being used by another
application that has its own security model or a PowerShell script has been embedded into
another application.
Undefined
When this execution policy is defined, it means that there is no execution policy set in
the current scope. If Undefined is the execution policy for all scopes, the effective execu-
tion policy is Restricted.
Setting the Execution Policy
By default, when PowerShell is first installed, the execution policy is set to Restricted. To
change the execution policy, you use the Set-ExecutionPolicy cmdlet, shown here:
PS C:\> set-executionpolicy AllSigned
Or, you can also use a Group Policy setting to set the execution policy for number of
computers. In a PowerShell session, if you want to know the current execution policy for a
machine, use the Get-ExecutionPolicy cmdlet:
ptg
PS C:\> get-executionpolicy
AllSigned
PS C:\>
Execution policies can not only be defined for the local machine, but can also be defined
for the current user or a particular process. These boundaries between where an execution
policy resides is called an execution policy scope. To define the execution policy for a
scope, you would use the Scope parameter for the Set-ExecutionPolicy cmdlet.
Additionally, if you wanted to know the execution policy for a particular scope, you
would use the Scope parameter for the Get-ExecutionPolicy cmdlet. The valid arguments
for the Scope parameter for both cmdlets are Machine Policy, User Policy, Process,
CurrentUser, and LocalMachine.
NOTE
The order of precedence for the execution policy scopes is Machine Policy, User Policy,
Process, CurrentUser, and LocalMachine.
PowerShell is a powerful tool that enables administrators to manage Windows platform
applications and to complete automation tasks. This section sheds some light on how
PowerShell’s many uses can be discovered and how it can be used to manage Windows
Server 2008 R2.
Using Windows PowerShell
733
Exploring PowerShell
21
Before using PowerShell, you might want to become more familiar with its cmdlets and
features. To assist administrators with exploring PowerShell, the PowerShell team decided
to do two things. First, they included a cmdlet that functions very similarly to how the
UNIX man pages function. Second, they also included a cmdlet that returns information
about commands available in the current session. Together, these cmdlets allow a novice
to tap into and understand PowerShell without secondary reference materials; explana-
tions of these cmdlets are discussed in the following sections.
Getting Help
The Get-Help cmdlet is used to retrieve help information about cmdlets, aliases, and from
help files. To display a list of all help topics this cmdlet supports, enter Get-Help * at the
PowerShell command prompt, as shown here:
PS C:\> get-help *
Name Category Synopsis
---- -------- --------
ac Alias Add-Content
asnp Alias Add-PSSnapin
ptg
clc Alias Clear-Content
cli Alias Clear-Item
clp Alias Clear-ItemProperty
clv Alias Clear-Variable
cpi Alias Copy-Item
cpp Alias Copy-ItemProperty
cvpa Alias Convert-Path
...
If that list seems too large to work with, it can be shortened by filtering on topic name
and category. For example, to get a list of all cmdlets starting with the verb Get, try the
command shown in the following example:
PS C:\> get-help -Name get-* -Category cmdlet
Name Category Synopsis
---- -------- --------
Get-Command Cmdlet Gets basic information...
Get-Help Cmdlet Displays information a...
Get-History Cmdlet Gets a list of the com...
Get-PSSnapin Cmdlet Gets the Windows Power...
Get-EventLog Cmdlet Gets information about...
Get-ChildItem Cmdlet Gets the items and chi...
Get-Content Cmdlet Gets the content of th...
...
PS C:\>
734
CHAPTER 21
Automating Tasks Using PowerShell Scripting
After selecting a help topic, that topic can be retrieved by using the topic name as the
parameter to the Get-Help cmdlet. For example, to retrieve help for the Get-Content
cmdlet, enter the following command:
PS C:\> get-help get-content
After executing this command, a shortened view of the help content for the Get-Content
cmdlet is displayed. To view the full help content, include the full switch parameter with
the command:
PS C:\> get-help get-content –full
After executing the command with the full switch parameter, you will find that the full
help content is divided into several sections. Table 21.3 describes each of these sections.
TABLE 21.3
PowerShell Help Sections
Help
Description
Section
Name
The name of the cmdlet
ptg
Synopsis
A brief description of what the cmdlet does
Description
A detailed description of the cmdlet’s behavior, usually including usage examples
Syntax
Specific usage details for entering commands with the cmdlet
Parameters
Valid parameters that can be used with this cmdlet
Inputs
The type of input this cmdlet accepts
Outputs
The type of data that the cmdlet returns
Notes
Additional detailed information on using the cmdlet, including specific scenarios
and possible limitations or idiosyncrasies
Examples
Common usage examples for the cmdlet
Related
References other cmdlets that perform similar tasks
Links
Get-Command
The Get-Command is used to gather basic information about cmdlets and other
commands that are available. For example, when executed, the Get-Command lists all the
cmdlets available to the PowerShell session:
Using Windows PowerShell
735
PS C:\> get-command
21
CommandType Name Definition
----------- ---- ----------
Cmdlet Add-Content Add-Content [-Path]
Cmdlet Add-History Add-History [[-InputObject] ...
Cmdlet Add-Member Add-Member [-MemberType]
Cmdlet Add-PSSnapin Add-PSSnapin [-Name]
Cmdlet Clear-Content Clear-Content [-Path]
