Windows Server 2008 R2 Unleashed (54 page)
Read Windows Server 2008 R2 Unleashed Online
Authors: Noel Morimoto

ptg
.
Management agent (MA)—
A FIM MA is a tool used to communicate with a
specific type of directory. For example, an Active Directory MA enables FIM to
import or export data and perform tasks within Active Directory.
.
Connected directory (CD)—
A connected directory is a directory that FIM commu-
nicates with using a configured MA. An example of a connected directory is an
Active Directory forest.
.
Connector namespace (CS)—
The connector namespace is the replicated informa-
tion and container hierarchy extracted from or destined to the respective connected
8
directory.
.
Metaverse namespace (MV)—
The metaverse namespace is the authoritative direc-
tory data created from the information gathered from each of the respective connec-
tor namespaces.
.
Metadirectory—
Within FIM, the metadirectory is made up of all the connector
namespaces plus the authoritative metaverse namespace.
.
Attributes—
Attributes are the fields of information that are exported from or
imported to directory entries. Common directory entry attributes are name, alias,
email address, phone number, employee ID, or other information.
FIM can be used for many tasks, but is most commonly used for managing directory entry
identity information. The intention here is to manage user accounts by synchronizing
238
CHAPTER 8
Creating Federated Forests and Lightweight Directories
attributes, such as logon ID, first name, last name, telephone number, title, and depart-
ment. For example, if a user named Jane Doe is promoted and her title is changed from
manager to vice president, the title change could first be entered in the HR or Payroll
databases; then through FIM MAs, the change could be replicated to other directories
within the organization. This ensures that when someone looks up the title attribute for
Jane Doe, it is the same in all the directories synchronized with FIM. This is a common
and basic use of FIM referred to as identity management. Other common uses of FIM
include account provisioning and group management.
NOTE
FIM is a versatile and powerful directory synchronization tool that can be used to sim-
plify and automate some directory management tasks. Because of the nature of FIM, it
can also be a very dangerous tool because MAs can have full access to the connected
directories. Misconfiguration of FIM MAs could result in data loss, so careful planning
and extensive lab testing should be performed before FIM is released to the production
directories of any organization. In many cases, it might be prudent to contact Microsoft
consulting services and certified Microsoft solution provider/partners to help an organi-
zation decide whether FIM is right for its environment, or even to design and facilitate
the implementation.
ptg
Exploring FIM Account Provisioning
FIM enables administrators to easily provision and deprovision users’ accounts and iden-
tity information, such as distribution, email and security groups across systems, and plat-
forms. Administrators will be able to quickly create new accounts for employees based on
events or changes in authoritative stores such as the human resources system. In addi-
tion, as employees leave a company, they can be immediately deprovisioned from those
same systems.
Account provisioning in FIM enables advanced configurations of directory MAs, along
with special provisioning agents, to be used to automate account creation and deletion in
several directories. For example, if a new user account is created in Active Directory, the
Active Directory MA could tag this account. Then, when the respective MAs are run for
other connected directories, a new user account could be automatically generated.
One enhancement of FIM over previous versions is that password synchronization is now
supported for specific directories that manage passwords within the directory. FIM
provides an application programming interface (API) accessed through the Windows
Management Instrumentation (WMI). For connected directories that manage passwords in
the directory’s store, password management is activated when an MA is configured in MA
Designer. In addition to enabling password management for each MA, Management Agent
Designer returns a system name attribute using the WMI interface for each connector
space object.
Synchronizing Directory Information with Forefront Identity Manager (FIM)
239
Outlining the Role of Management Agents (MAs) in FIM
An MA links a specific connected data source to the metadirectory. The MA is responsible
for moving data from the connected data source and the metadirectory. When data in the
metadirectory is modified, the MA can also export the data to the connected data source
to keep the connected data source synchronized with the metadirectory. Generally, there
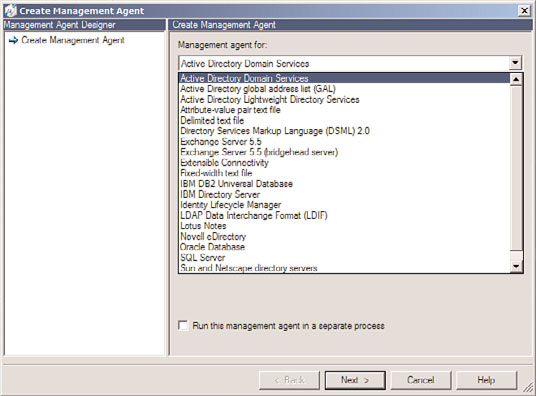
is at least one MA for each connected directory. FIM includes MAs for multiple directory
sources, as shown in Figure 8.9.
ptg
FIGURE 8.9
Potential management agents for FIM.
8
NOTE
FIM includes integrated support for synchronization with additional directories such as
SAP, Oracle, IBM, and Sun. In addition, it also introduced the ability for end users to
reset their own passwords via a web management interface.
MAs contain rules that govern how an object’s attributes are mapped, how connected
directory objects are found in the metaverse, and when connected directory objects
should be created or deleted.
These agents are used to configure how FIM will communicate and interact with the
connected directories when the agent is run. When an MA is first created, all the configu-
ration of that agent can be performed during that instance. The elements that can be
240
CHAPTER 8
Creating Federated Forests and Lightweight Directories
configured include which type of directory objects will be replicated to the connector
namespace, which attributes will be replicated, directory entry join and projection rules,
attribute flow rules between the connector namespace and the metaverse namespace, plus
more. If a necessary configuration is unknown during the MA creation, it can be revisited
and modified later.
Defining FIM and Group Management
Just as FIM can perform identity management for user accounts, it also can perform
management tasks for groups. When a group is projected into the metaverse namespace,
the group membership attribute can be replicated to other connected directories through
their MAs. This enables a group membership change to occur in one directory and be
replicated to other directories automatically.
Installing FIM with SQL 2005/2008
FIM requires a licensed version of SQL Server 2005 or 2008 to run, and an install of the
product will prompt for the location of a SQL server.
It is not necessarily required to install a new instance of SQL because an existing SQL farm
can be used as well. If an existing SQL 2005/2008 server is not available, SQL can be
installed on the same system as FIM.
ptg
Harnessing the Power and Potential of FIM
FIM is a very capable and powerful tool. With the right configuration and some fancy
scripting, it can be configured to perform an incredible variety of automatic tasks.
Today’s environments are rife with directories, which increase the amount of administra-
tion required to create accounts, delete accounts, and update user information manually.
FIM can greatly ease these requirements, improving administration and security. The
next section focuses on some of the most valuable capabilities of FIM and how to effec-
tively use them.
Managing Identities with FIM
FIM can be used for the most basic and easiest configurations. For example, FIM can be
used to synchronize identity information between accounts in different directories.
Identity information could include names, email and physical addresses, titles, depart-
ment affiliations, and much more. Generally speaking, identity information is the type of
data commonly found in corporate phone books or intranets. To use FIM for identity
management between Active Directory and an LDAP directory server, follow these high-
level steps:
1. Install the Metadirectory services component of FIM.
2. Create a management agent for each of the directories, including an Active Directory
management agent and an LDAP agent.
3. Configure the management agents to import directory object types into their respec-
tive connector namespaces.
Harnessing the Power and Potential of FIM
241
4. Configure one of the management agents—for example, the Active Directory MA—
to project the connector space directory objects and directory hierarchy into the
metaverse namespace.
5. Within each of the management agents, a function can be configured called
attribute flow to define which directory object attributes from each directory will be
projected into the respective metaverse directory objects. Configure the attribute
flow rules for each management agent.
6. Configure the account-joining properties for directory objects. This is the most
crucial step because it will determine how the objects in each directory are related to
one another within the metaverse namespace. To configure the account join, certain
criteria such as an employee ID or first name and last name combination can be
used. The key is to find the most unique combination to avoid problems when two
objects with similar names are located—for example, if two users named Tom Jones
exist in Active Directory.
7. After completely configuring the MAs and account joins, configure management
agent run profiles to tell the management agent what to perform with the connected
directory and connector namespace. For example, perform a full import or an export
of data. The first time the MA is run, the connected directory information is
imported to create the initial connector namespace.
ptg
8. After running the MAs once, they can be run a second time to propagate the author-
itative metaverse data to the respective connector namespaces and out to the con-
nected directories.
These steps can be used to simplify account maintenance tasks when several directories
need to be managed simultaneously. In addition to performing identity management for
user accounts, FIM can also be used to perform management tasks for groups. When a
group is projected into the metaverse namespace, the group membership attribute can be
replicated out to other connected directories through their management agents. This
allows a group membership change to occur in one directory and be replicated to other
directories automatically.
8
Provisioning and Deprovisioning Accounts with FIM
Account provisioning in FIM allows advanced configurations of directory management
agents, along with special provisioning agents, to be used to automate account creation
and deletion in several directories. For example, if a new user account is created in Active
Directory, the Active Directory MA could tag this account. Then, when the respective MAs
are run for other connected directories, a new user account can be automatically generated
in those other accounts.
The provisioning and deprovisioning process in FIM can be an extremely useful tool in
situations where automatic creation and deletion of user accounts is required. For
example, a single user account can be created in an HR Oracle database, which can initiate
a chain-event of account creations, as illustrated in Figure 8.10.
242
CHAPTER 8
Creating Federated Forests and Lightweight Directories
Phone SQL DB:
James Mills
NDS Username:
x4388
JMills
AD LDS Username:
JAMES
FIM Metaverse
AD LDS2 Username:
HR Oracle Database Record:
FIM
MillsJ
Lastname=Mills
Person object
Firstname=James
JobTitle=Director of IT
Extension=x4288
EmployeeID=12345678
ptg
AD/Exchange 2007 UPN:
