Pro Puppet (25 page)
Authors: Jeffrey McCune James Turnbull

The problem of scaling HTTP-based web services to tens of thousands of clients has been around for quite some time. There are many technical solutions provided by commercial products like Citrix NetScaler, Cisco IOS, and F5 BIG-IP. Many open-source software projects also exist, including Apache itself, HAProxy, Nginx, and Pound. Puppet fits into the overall problem of HTTP load balancing nicely because of its use of SSL and HTTP for communication.
We’re going to build upon the single Puppet master configuration we just created and then split the work across two Puppet master systems. We’ll use the Apache Web server to handle the incoming Puppet agent requests and route them to an available back-end Puppet master. If we require additional capacity, we can add additional Puppet master processes. This configuration has the added benefit of high availability. If a particular Puppet master system has trouble or needs to be taken out of service, the front-end load balancer will stop routing Puppet agent requests to that master process.
We’re going to configure two Puppet master Apache virtual hosts, much like the virtual host we created in the previous section. However, there is one important difference: we will disable SSL for the Apache virtual hosts. Instead, we’ll configure a new front-end Apache virtual host to authorize incoming Puppet agent requests and handle the SSL encryption and decryption of the traffic. This front-end load balancer will terminate the SSL connection, be responsible for authenticating the Puppet agent request and then present this authentication information to the back-end Puppet master workers for authorization.
You’ll see how Apache is able to pass the authentication information along through the use of client request headers, and how the back-end virtual hosts are able to set environment variables for the Puppet master based on the values of these client request headers.
 Caution
Caution
It is important to keep in mind that the load-balancing configuration discussed in this section authorizes and terminates SSL connections at the load balancer. All traffic between the front-end load balancer and the back-end Puppet master systems are therefore unencrypted and in plain text. Requests directly to the worker virtual hosts may easily be forged and should only be allowed from the load balancer. If this is an unacceptable configuration for your environment, please consider using a TCP load balancer in order to preserve and pass through the SSL encryption to the back-end Puppet master virtual hosts.
When running the Puppet master behind a load balancer, there will be multiple Puppet master processes running on different hosts behind the load balancer. The load balancer will listen on the Puppet port of 8140. Incoming requests will be dispatched to available back-end worker processes, as illustrated in
Figure 4-1
. The example configuration presented in this chapter configures the Puppet CA and workers all on the same host using unique TCP ports bound to the loopback interface.
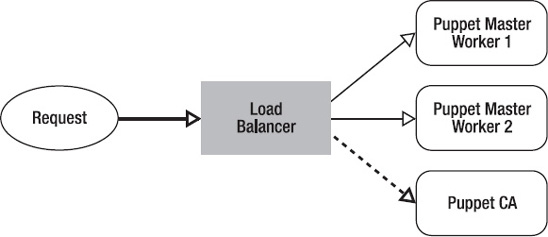
Figure 4-1.
Puppet master workers
To get started with our load-balancing configuration, you’ll copy the existing Puppet master virtual host we configured in the previous section into two additional virtual host configurations. Each of these two virtual hosts will have SSL disabled. You’ll then create a third virtual host listening on the standard Puppet master port of 8140 with SSL enabled. This virtual host will forward a request to any available back-end virtual host.
First, move the existing Puppet master to port 8141 to free up port 8140 for the new front-end load balancer virtual host. To do this, update the Listen and VirtualHost configuration items in the Apache Puppet master configuration, in our case in the20_puppetmaster.conffile we created earlier:
Listen 8141
# Moved the Puppet master stand alone to port 8141.
# The Load balancer listens on the standard Puppet master port
This change to the virtual host only required two small edits to the TCP port configuration in20_puppetmaster.conf.
Next, create a new Puppet master virtual host configuration for the first back-end worker in/etc/httpd/conf.d/40_puppetmaster_worker_18140.conf.
In
Listing 4-9
, we configure a unique RackDocumentRootin order to uniquely identify the first Puppet master worker. Commands such aspassenger-statusidentify processes by their configuredDocumentRoot.
Listing 4-9.
First Apache Puppet master worker virtual host configuration file
# cat 40_puppetmaster_worker_18140.conf
Listen 18140
SSLEngine off
# Obtain Authentication Information from Client Request Headers
SetEnvIf X-Client-Verify "(.*)" SSL_CLIENT_VERIFY=$1
SetEnvIf X-SSL-Client-DN "(.*)" SSL_CLIENT_S_DN=$1
RackAutoDetect On
DocumentRoot
/etc/puppet/rack/puppetmaster_18140//files/06/21/01/f062101/public/
/>
Options None
AllowOverride None
Order allow,deny
allow from all
In addition to the configuration file, you need to duplicates the Rack configuration directory into the newDocumentRootlocation (see
Listing 4-10
).
Listing 4-10.
Create the first Puppet master worker rack configuration
# rsync -avxH /etc/puppet/rack/puppetmaster{,_18140}/
building file list ... done
created directory /etc/puppet/rack/puppetmaster_18140
./
config.ru
/files/06/21/01/f062101/public/
tmp/
sent 621 bytes received 60 bytes 1362.00 bytes/sec
total size is 431 speedup is 0.63
Note the trailing slash in thersynccommand, which is important and ensures that the directory contents are copied into one another.
 Caution
Caution
The back-end worker process is listening on the local interface of 127.0.0.1. This prevents network systems from reaching the unencrypted, plain text back-end worker virtual host. In a production deployment, the back-end virtual host is often on a different machine than the front-end load balancer. Care must be taken to ensure the unencrypted traffic is secure and protected. In general, the back-end virtual host should not accept connections from any machine other than the front-end load balancer.
After we configure the first back-end Puppet master worker, we need to configure the front-end virtual host. This front-end virtual host is going to perform a number of tasks:
- Terminate the SSL connection
- Authenticate the client request
- Set the authentication information in client request headers
- Pass the request along to one of the available back-end worker processes.
The configuration file for the front-end load balancer is very similar to the original Apache Passenger configuration file with the addition of a reverse proxy stanza and the removal of the Passenger and Rack configuration stanzas (
Listing 4-11
).
Listing 4-11.
Apache front-end load balancer configuration file
# cat 30_puppetmaster_frontend_8140.conf
# Available back-end worker virtual hosts
# NOTE the use of cleartext unencrypted HTTP.
BalancerMember
http://127.0.0.1:18140
BalancerMember
http://127.0.0.1:18141
Listen 8140
SSLEngine on
# SSLCipherSuite SSLv2:-LOW:-EXPORT:RC4+RSA
SSLProtocol -ALL +SSLv3 +TLSv1
SSLCipherSuite ALL:!ADH:RC4+RSA:+HIGH:+MEDIUM:-LOW:-SSLv2:-EXP
# Puppet master should generate initial CA certificate.
# ensure certs are located in /var/lib/puppet/ssl
SSLCertificateFile /var/lib/puppet/ssl/certs/puppet.example.com.pem
SSLCertificateKeyFile /var/lib/puppet/ssl/private_keys/puppet.example.com.pem
SSLCertificateChainFile /var/lib/puppet/ssl/certs/ca.pem
SSLCACertificateFile /var/lib/puppet/ssl/ca/ca_crt.pem
# CRL checking should be enabled
# disable next line if Apache complains about CRL
SSLCARevocationFile /var/lib/puppet/ssl/ca/ca_crl.pem
# optional to allow CSR request, required if certificates distributed to client during
provisioning.
SSLVerifyClient optional
SSLVerifyDepth 1
SSLOptions +StdEnvVars
# The following client headers record authentication information for down stream workers.
RequestHeader set X-SSL-Subject %{SSL_CLIENT_S_DN}e
RequestHeader set X-Client-DN %{SSL_CLIENT_S_DN}e
RequestHeader set X-Client-Verify %{SSL_CLIENT_VERIFY}e
SetHandler balancer-manager
Order allow,deny
Allow from all
ProxyPass / balancer://puppetmaster/
ProxyPassReverse / balancer://puppetmaster/
ProxyPreserveHost On
There are three main differences between the front-end load balancer configuration file in
Listing 4-11
and the stand-alone Apache Puppet master configuration in
Listing 4-6
. At the top of the load balancer virtual host configuration, a pool of back-end virtual hosts is defined in theProxystanza. Notice that two virtual hosts are listed, port 18140 and port 18141, even though we have only configured the one listening on port 18140 so far.
Part of the responsibility of the front-end load balancer is to determine if each back-end worker is online and available to handle requests. Since no worker virtual host is available on port 18141 yet, the front-end virtual host will automatically take http://127.0.0.1:18141 out of rotation until it becomes available. The Puppet agent nodes will not see an error message unless all back-end worker virtual hosts are marked as offline.
In addition to defining the list of back-end worker virtual hosts, theProxystanza gives the namebalancer://puppetmasterto the collection. When additional back-end virtual hosts are added to the system, they should be listed using theBalancerMemberkeyword in theProxystanza. Once listed, they’ll automatically be added to the rotation of back-end workers used by the front-end virtual host listening on port 8140.
The second important section of the front-end virtual host configuration file is the threeRequestHeaderlines. These three configuration statements configure the front-end load balancer to set three client request headers containing authentication information. When a back-end Puppet master virtual host receives a client request from the load balancer, it will inspect these client request headers and set environment variables based on their contents. The Puppet master process will look to these environment variables while authorizing the Puppet agent request.
For the Puppet agent running onmail.example.com, the client request headers used for authentication look as shown in
Listing 4-12
.
Listing 4-12.
Puppet agent authentication and authorization request headers
X-SSL-Subject: /CN=mail.example.com
X-Client-DN: /CN=mail.example.com
X-Client-Verify: SUCCESS
