Reverse Deception: Organized Cyber Threat Counter-Exploitation (58 page)
Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers

Drive-by downloads
This approach typically involves a website that attempts to fake you into installing a specific add-on or module that, based on the name, looks benign but is actually an unsigned (uncertified or not an official release) and modified version of the real application (or not) that installs something nefarious onto your system.
Client-side exploits
This type of attack has been the most well executed over the past decade with great success by the bad guys and the good guys. This occurs when users visit a website and upon identification of their operating system, browser, browser add-ons, or installed applications, an exploit is attempted if they are running a vulnerable version.
Phishing
This has been one of the most effective exploitation methods for more than a decade. Whether the phishing e-mail is opportunistic or targeted, it is very effective and can come in many forms. Phishing schemes can target an organization’s employees, leadership, or multiple personnel at once. When employee accounts are used to target leadership, this is called
vertical phishing
. When the accounts are used to target the employee’s colleagues and peers, this is known as
horizontal phishing
. All of the information is in the victim’s e-mail contacts list stored on the targeted system. Certain individuals, such as C-level executives, sales managers, and marketing directors, provide more details about their contacts, including their company, role, numbers, addresses, and other specifics that help the bad guys.
Shortened URLs
This little bit of “fun” (insert sarcasm) has been the bane of many security professionals for the past few years. As social networks have grown in popularity, so has the demand for shortened URLs (most social network blogs have about a 100-character URL limitation), which help obfuscate blogs or content of specific opinions or links. These seemingly innocuous links can lead to doom, as they might take you to a malicious site hosting an exploit kit, exploit pack, or any number of client-side exploitation tools or techniques.
Over the past decade, vendors have been selling bootleg and backdoored hardware and software to companies and organizations around the world. There are even solutions that monitor your hardware from another piece of hardware. This has been a critical injection point into many networks and enterprises over the years.
Social engineering is one of the oldest methods but is still the most effective. The only difference is the approaches and techniques that have evolved along with criminal operations, especially when it comes to online crime.
Years ago, you could hack in to and knock over a system, and easily pump and dump the system or network without getting caught. You could call into an organization and extract whatever information you needed from almost anyone you got on the phone. There was also dumpster-diving, which is the process of rummaging through your victim’s trash dumpsters for sensitive or precious network information carelessly thrown out by one of the personnel of the victim organization. However, with the evolution of hacking, IT organizations have become more paranoid. Today, there are many more layers and information systems between the criminal and the victim. This has raised the bar for the hacking game in 2012 and drawn criminals from directly hacking into systems to begin leveraging more modern techniques, such as exploit kits and client-side exploitation of victim systems.
Why is social engineering still so successful? This is primarily due to the rapid evolution of technology and the associated additional features and options available for every system that has third-party applications and tools and the inability for “the masses” in the IT sector to keep up with every facet or nuance of their enterprise system “features” (which are meant to add richness to modern third-party programs), which inherently come with additional vulnerabilities and exploitable weaknesses. Not every single professional can be an expert on all facets of their enterprise, unless they run a very small enterprise (less than 50 users). For those of us who maintain security and counter operations of massive enterprises that we manage for ourselves or for our customers, we leverage communities of experts who share information about threats and adversaries on private vetted mailing lists. To learn more about some of the subject matter experts, refer to
Chapter 13
.
Social engineering comes just not in a phone call or someone walking into your organization anymore. Today, social engineering comes in the form of fake websites, fake programs, fake games, and fake e-mail messages with malicious attachments, links, or content. All of these more modern techniques rely on the victim taking action (to “click”) to allow the threat to execute or embed itself in your computer. So not understanding everything about your enterprise
is
alright, as long as you leverage internal or external resources who do understand the areas of the organization’s infrastructure you are unfamiliar with. Although learning as much as you can is always recommended, there are experts available to help you through times of troubles.

Meet the Team
Years ago, small groups working together or lone wolves (ninjas) were the ones who hacked into systems. The days of old have come and gone, and the criminals are now working together without fear of impunity more than ever. The lone-wolf approach is becoming history, as it is easier and safer to work in numbers on the Internet, especially since evidence collection and attribution are so difficult for all involved parties, including law enforcement and intelligence agencies.
Today, a number of groups will participate in an attack. It is like a professional tradecraft, as each member of the criminal network must play his part perfectly in order to maintain the hackers’ number-one rule: Never get caught. Criminals communicate through coordinated systems, forums, and other methods. They have the ability to discuss, plan, and carry out their operations in secret.
Many hands are involved in stealing information from your users and your enterprise. The following illustrates the members of a modern criminal team.
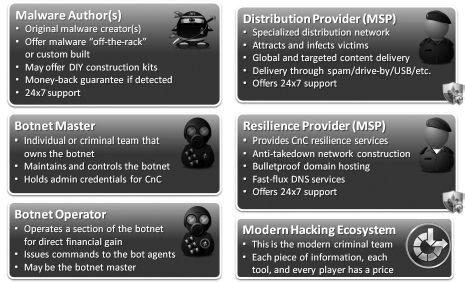
Modern cyber criminal organizational structure and breakdown
Let’s meet each of the groups that make up the modern criminal threat.
Malware author
This is typically one person or several people working in a tight-knit group. Malware authors only share their raw source code internally and protect it well as pirates of old protected their stolen booty. Their code is sold directly to bot masters, and the number of buyers depends on the level of caution of the author team. Some authors develop crimeware that is meant to be used repeatedly for numerous short-duration campaigns. Others focus on malware designed for stealing more critical information and that will maintain persistence on victims’ systems for longer periods of time (months or years).
Botnet master
This is generally the “man (or woman) with the plan” who set up an infrastructure to support a crimeware network. Botnet masters may use a specific family of malware, or if they are a little more concerned with long-term operations and a little smarter, they will rely on multiple families of malware that operate at different levels of functionality. Botnet masters also typically set up the affiliate sites, interact with partners (distribution and resilience providers), and run the operations team (all the way down to the setup of the money-mule framework, which is a network for moving money electronically throughout the Internet so it is laundered or accessible to the criminal who has stolen from the victim). This is the level most law enforcement groups go for, as the botnet masters are easier to find than the malware authors. If they can apprehend the botnet masters and use enough leverage, they should be able to jump to the authors with some ease.
