Reverse Deception: Organized Cyber Threat Counter-Exploitation (60 page)
Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers

The highest scan speed on the market—increases attacker agility
The following is an example of another legitimate service that is regularly abused. It offers online encryption services to help members of the forums efficiently protect their binaries from detection of antivirus or security systems. It is a free service, and the binaries protected here are not submitted to antivirus firms, which is common practice among more professional binary analysis online systems (such as VirusTotal, ThreatExpert, and Anubis), which are in turn analyzed and pushed back down to antivirus host-based subscribers. Finally, we would like to point out that upon visiting this page, you are not prompted to log in, which means it is free to anyone.
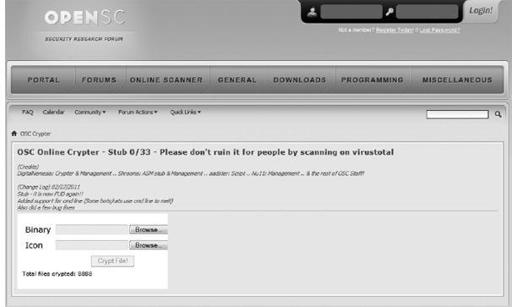
OpenSC.WS
online binary crypter
As you can see in the following screenshot, from a 2012 comment, it appears that our hypotheses turned out to be correct. As it’s a free service available to anyone, the volume of criminals and researchers who are using this online tool is so large in comparison to other paid-for armoring suites that the tool’s ability to remain undetectable is being hindered, apparently dramatically.
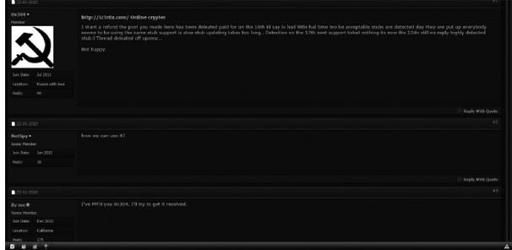
OpenSC.WS
online binary crypter recent comments
The following site is highly recommended on numerous underground forums as a reliable source for their customer privacy and reliability. You can pay to have your binaries, data, and many other security and protection services available without too much trouble, through your own personalized online member portal.
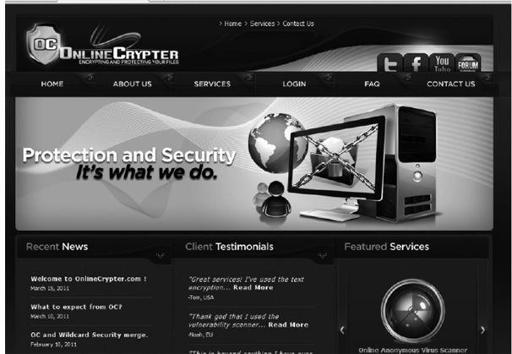
OC online binary crypter home page
Academic Research Abuse
Academic research projects can also help the bad guys. These give both opportunistic and targeted attackers a few aids: the ability to predefine IP address ranges to not function within, which IP address ranges to not accept connections from, and where not to scan. There are network ranges and attribution of some security companies, provided in a most efficient manner.
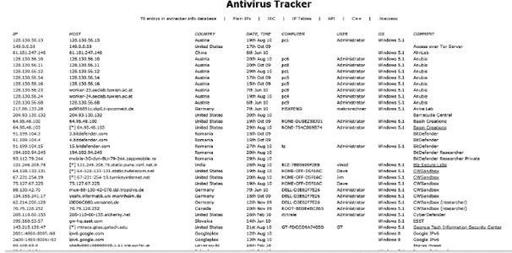
AntiVirus Tracker, tracking antivirus and security firm malware labs
Here is the rest of the page from the preceding image. This illustrates why they do what they do, how they do it, and most important, how they feel about it (motivation and intent).

AntiVirus Tracker, information on the group of academics who support the project
Circles of Trust
Curious entrepreneurs even have circles of trust, like organized and motivated criminals. The information is out there; you simply need to go look for it and share. The more you share, the more you are accepted by the groups who hang out and regularly post to most of these sites and forums.
Timeliness is very important, as the more regular of a member you are, the more you are accepted by the mass of the group. You also need to remember that what times of day you share are important, as it may become suspicious if you are only sharing during business hours. Keep in mind that the bad guys have their own circles of trust, and they share based on thought leadership, presentation of skill by oneself, and public demonstration of domain knowledge. Sometimes simply communicating is enough to enter a circle of trust. This trust model can be exploited, as it is clearly apparent even the most organized cyber criminals communicate on the Internet and post in forums. You just need to inject yourself into that flow of thoughts and build up some circles.
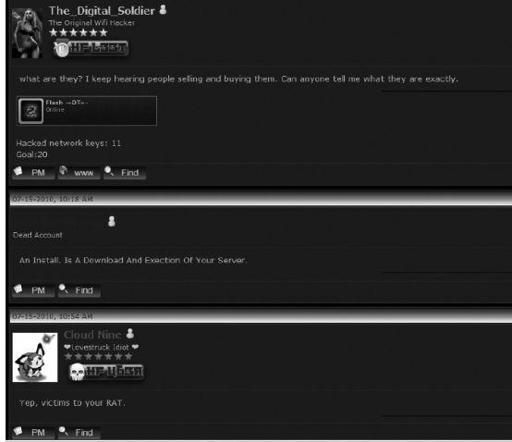
Underground forum post of someone asking a legitimate question and receiving solid answers
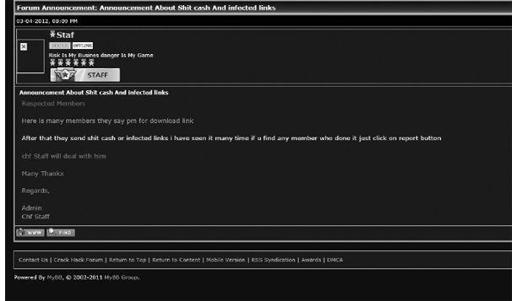
Underground forum post of administrators warning of scams to members
In some cases, the underground hacker culture has its own code of ethics and rules, especially when it comes to burning or scamming another peer in the community. The following screenshots show where various individuals or groups have complained about another underground cyber culture member being a ripper (a common underground term for someone who rips off others by providing a promised good or service from another member of the community). This can help a lot of individuals and groups from making bad deals on the underground.
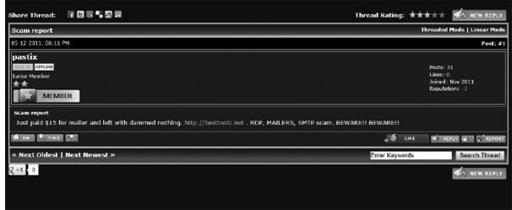
Underground forum post of a member warning other members of a ripper

