Reverse Deception: Organized Cyber Threat Counter-Exploitation (81 page)
Read Reverse Deception: Organized Cyber Threat Counter-Exploitation Online
Authors: Sean Bodmer
Tags: #General, #security, #Computers

Inside enclave
Next to critical assets
Key avenues of approach
The following architecture types are available for production-based honeynets:
Centralized
All components are centrally housed in one physical location, as shown in
Figure 8-4
.
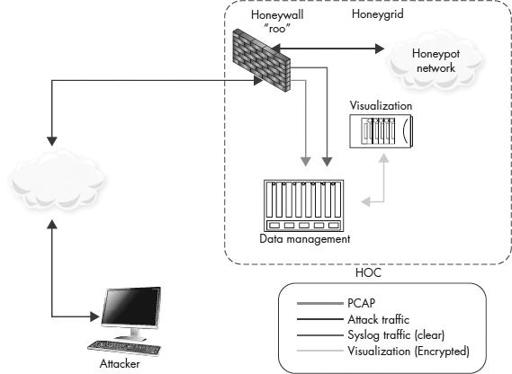
Figure 8-4
Centralized architecture
Distributed
All components are geographically dispersed across multiple sites, as shown in
Figure 8-5
.
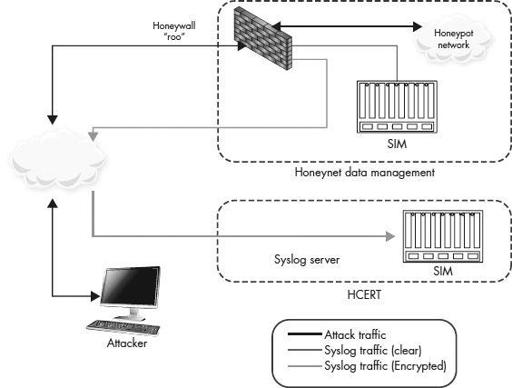
Figure 8-5
Distributed architecture
Federated
All components are trusted and have direct access between the sensor and the manager, as shown in
Figure 8-6
.
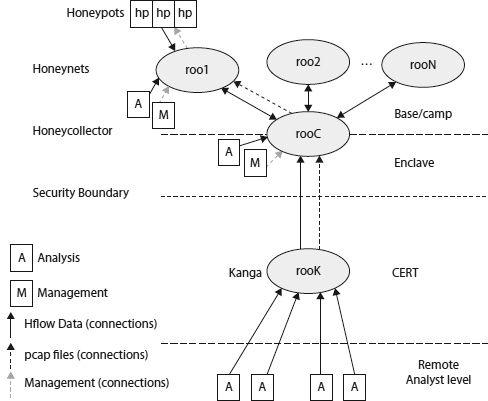
Figure 8-6
Federated architecture
Confederated
All components have varying levels of trust and have restricted access between the sensor and manager, as shown in
Figure 8-7
.
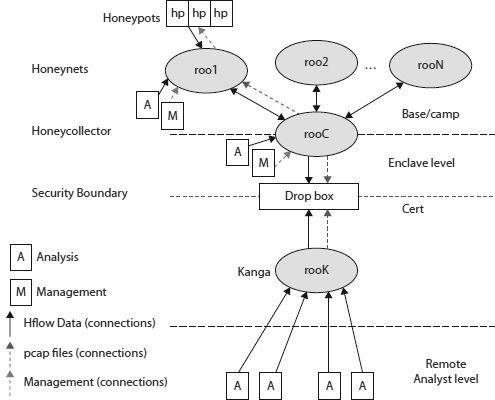
Figure 8-7
Confederated architecture
Centralized deployments are the most effective in small to large enterprises and easily scalable. In a centralized architecture, all of the data is local and can be easily accessed. However, when requirements mandate a distributed architecture in the event of network failure or latency, data can be lost or not received in a timely manner to ensure the focus believes in the perceptual consistency of your deception. This type of architecture can sometimes disrupt your ability to effectively respond to threats, which, in effect, reduces the value of a production honeynet.
Honeywall Accreditation
Currently, the honeywall is DoD Information Technology Security Certification and Accreditation Process (DITSCAP) accredited through the Defense Information Systems Agency. The honeywall has specific versions available to operate on US government networks who still accept the DITSCAP certification standard.
Not every version of the honeywall operating system (roo) is accredited. Only specific versions with an accompanying Security Readiness Review (SRR) are available for use. However, the accreditation boundary of the honeywall allows for honeynets freely running and operating within production networks.
Content Staging
There are indicators on all machines that users regularly use any given system. The method of content staging is important when configuring your honeypots (sensors) prior to deployment.
Ensuring that the correct information is on your honeypots is critical from the beginning. Attackers will expect information to be on any organizational system. You must ensure the right data is on the honeypot to entice the attacker to interact with your honeypot for as long as possible.
The following are some items that need to be addressed when performing initial content staging of a honeypot.
Files
When setting up files, make sure the following types of files are on a system and
continue
to be added to the system as a common computer user. So, whether you want to protect your files or generate a perceptually consistent deception, these files should be updated
at least
every 48 hours in order to ensure perceptual consistency of a light casual computer user. Remember, perceptual consistency to a remote attacker can be everything. These files are the files a remote Trojan, bot, or crimeware will look through for specific keywords and some will generate keywords based on certain data types. Here is a short list of the major file types that will be searched for. They are present everywhere.
