Windows Server 2008 R2 Unleashed (121 page)
Read Windows Server 2008 R2 Unleashed Online
Authors: Noel Morimoto

an ADM subfolder to store all the legacy administrative template files referenced and
imported into the GPO.
registry.pol Files
ptg
Within a particular group policy, the settings are segmented into several sections. Many
settings with the GPO configure keys and values within the Registry. The configuration
status and value of these settings are stored within the registry.pol files in either the User
or Machine subfolders. The registry.pol file contains only the configured settings within
the GPO to improve processing.
gpt.ini File
When a GPO is created, a folder for the GPO is created within the connected domain
controller’s sysvol folder. At the root of that GPO folder is a file named gpt.ini. This file
contains the revision number of the GPO. The revision number is used when a GPO is
processed by a computer or user object. When a GPO is first processed, the revision
number is stored on the system and when subsequent GPO processing occurs, the refer-
ence number in the gpt.ini file is compared with the stored value on the local system
cache. If the number has not changed, certain portions of the GPO are not processed.
19
There are, however, certain portions of a GPO that are always processed, like scripts.
Each time a GPO is changed, the reference or revision number is increased, and even
though the gpt.ini file contains a single number, it actually represents a separate revision
number for the computer and user section of the GPO.
The default configuration of not processing certain GPO sections if the revision number
has not changed can be overridden. In some cases, even though the GPO has not
changed, the intended settings could have been changed by the user or a program and
sometimes forcing the entire GPO to always be processed is required.
This configuration setting is available in both the Computer Configuration and User
Configuration nodes of the GPO and is discussed later in Chapter 27.
594
CHAPTER 19
Windows Server 2008 R2 Group Policies and Policy Management
Group Policy Administrative Templates
GPO administrative templates are, in most cases, a set of text or Extensible Markup
Language (XML)–based files that include clearly defined settings that can be set to a
number of different values.
Administrative templates are provided to give administrators easy access to many config-
urable settings commonly used to manage server and workstation computers and end users.
When a new GPO is created, a base set of administrative templates are imported or refer-
enced within that policy. Additional administrative templates can be imported to a partic-
ular policy to add functionality as required.
Windows 7 and Windows Server 2008 R2 Central Store
As stated earlier in this chapter, each GPO in the Active Directory forest will have a corre-
sponding folder stored in the sysvol folder on each domain controller in the domain in
which the GPO is created. If the domain controllers in the particular domain are running
Windows Server 2003, each of these GPO folders would contain a copy of each of the
administrative templates loaded in that particular GPO. This created many duplicated
administrative template files and required additional storage space and increased replica-
tion traffic.
ptg
Starting with the new Group Policy infrastructure included with Windows Vista and
Windows Server 2008 and continuing with Windows 7 and Windows Server 2008 R2,
newly created GPOs only store the files and folders required to store the configured
settings, scripts, registry.pol, and other GPO-related files. When the GPO is opened for
editing or processed by a Windows Vista, Windows 7, Windows Server 2008, or Windows
Server 2008 R2 computer, the local copy of the administrative templates is referenced but
not copied to the new GPO folder in sysvol. Instead, the administrative templates are
referenced from files stored on the local workstations or the domain central store.
The GPO central store is a file repository that houses each of the next generation adminis-
trative templates. The central store would contain all of the new ADMX and ADML
administrative templates and each workstation would reference the files on the domain
controller they are using to process group policies. With a central store created, when a
GPO is opened or processed, the system first checks for the existence of the central store
and then only uses the templates stored in the central store.
The GPO central store can be created within Active Directory infrastructures running any
version of Windows Server 2003, Windows Server 2008, or Windows Server 2008 R2
domain controllers.
Starter GPOs
Windows Server 2008 and Windows Server 2008 R2 Group Policy Management Console
provide a new feature of GPO management called starter GPOs. Starter GPOs are similar to
regular GPOs, but they only contain settings available from administrative templates. Just
as security templates can be used to import and export the configured settings within the
security section of a policy, starter GPOs can be used to prepopulate configured settings in
Elements of Group Policy
595
the Administrative Templates sections of the Computer Configuration and User
Configuration nodes within a GPO. After the release of Windows Server 2008 and
included in Windows Server 2008 R2, Microsoft released a set of predefined starter GPOs
for Windows Vista and Windows XP. The predefined settings in these starter GPOs are
based on information that can be found in the Windows XP and Windows client security
guide published by Microsoft. These particular starter GPOs are read-only policies, but
administrators can create their own starter GPOs as needed by the organization.
How to enable starter GPO functionality and how to create and manage starter GPOs are
covered later in this chapter in the section, “Creating and Utilizing Starter GPOs.”
Policy Settings
Policy settings are simply the configurable options made available within a particular
GPO. These settings are provided from the base administrative templates, security settings,
scripts, policy-based QOS, and, in some cases, software deployment packages. Many policy
settings correspond one to one with a particular Registry key and value. Depending on the
particular settings, different values, including free-form text, might be acceptable as a
legitimate value.
GPO policy settings are usually configurable to one of three values: not configured,
ptg
enabled, or disabled. It is very important for administrators to understand not only the
difference among these three values, but to also understand what the particular policy
setting controls. For example, a policy setting that disables access to Control Panel will
block access to Control Panel when enabled but will allow access when disabled.
GPO policy settings apply to either a computer or a user object. Within a particular GPO,
an administrator might find the same policy setting within both the Computer
Configuration and User Configuration nodes. In cases like this, if the policy setting is
configured for both objects, the computer setting will override the user setting if the
policy is linked to the user object and the workstation to which the user is logged on.
Preference Settings
Group Policies have two main setting nodes, including the Computer and User
Configuration nodes. Each of these contains two main nodes as well, the Policies and
19
Preferences setting nodes. The group policy extensions presented in the Preferences node
provide administrators with the ability to configure many default or initial configuration
and environmental settings for users and computers. One really great feature of GPO
Preferences is Item-Level Targeting, which only applies a certain preference, such as setting
the Start menu on Windows 7 workstations to configure the power button to perform a
logoff instead of a computer shutdown, to only defined users or groups within the Item-
Level Target definition of that GPO. When a user logs on to a workstation and has that
preference applied, this will be the initial setting, but users would be able to change that
setting if they desire. One important distinction that all GPO administrators must make is
that policies set and enforce settings, whereas preferences configure initial settings but do
not block the settings from changes. More information on GPO preferences is detailed in
Chapter 27.
596
CHAPTER 19
Windows Server 2008 R2 Group Policies and Policy Management
Group Policy Object Links
GPO links are the key to deploying GPOs to a predetermined set of Active Directory
computers and/or users. GPO links define where the particular policy or policies will be
applied in terms of the Active Directory domain and site hierarchy design.
GPOs can be linked to Active Directory sites, domains, and organizational units (OUs).
Also, a single GPO can be linked to multiple sites, domains, and OUs in a single forest.
This gives administrators the flexibility to create a single policy and apply it to several
different sets of computers and users within an Active Directory forest.
The design of the Active Directory infrastructure, including site design, domain and tree
design, and OU hierarchy, is critical to streamlining targeted GPO application. Careful
planning and consideration should be taken into account during the Active Directory
design phase with regard to how GPOs will be used and how user, group, and computer
objects will be organized.
GPO links can also be disabled as required, to assist with troubleshooting GPO application
or processing.
Group Policy Link Enforcement
Microsoft provides administrators with many ways to manage their infrastructure, includ-
ptg
ing forcing configurations down from the top. GPO link “enforcement,” historically known
as “No Override,” is an option of a GPO link that can be set to ensure that the settings in a
particular policy will be applied and maintained even if another GPO has the same setting
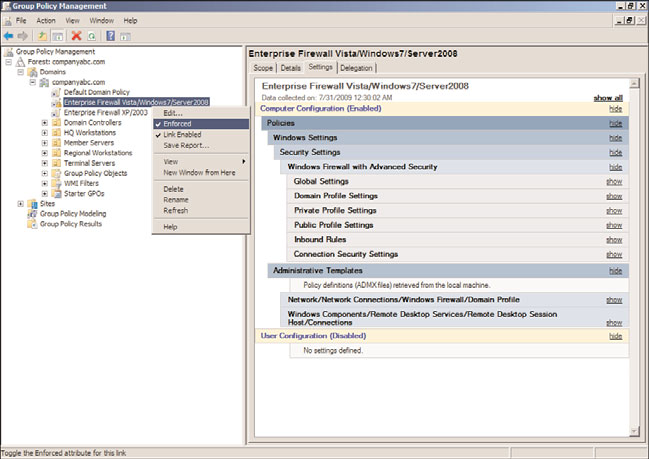
configured with a different value. GPO link enforcement is shown in Figure 19.5.
FIGURE 19.5
Enforcing a group policy.
Elements of Group Policy
597
This function should be used with caution because it might result in undesired functional-
ity or a different level of security than what is required to run a particular service or appli-
cation or manage a system. Before enabling GPO enforcement on any policy, carefully
research and test to ensure that this will not break any functionality or violate an organi-
zation’s IT or regulatory policy.
Group Policy Inheritance
GPOs can be linked at the site, domain, and multiple OU levels. When an Active
Directory infrastructure contains GPOs linked at the domain level, as an example, every
container and OU beneath the domain root container inherits any linked policies. As a
default example, the “Domain Controllers” OU inherits the default domain policy from
the domain.
GPO inheritance allows administrators to set a common base policy across an Active
Directory infrastructure while allowing other administrators to apply more granular poli-
cies at a lower level that apply to subsets of users or computers. As an example of this, a
GPO can be created and linked at the domain level that restricts all users from running
