Windows Server 2008 R2 Unleashed (171 page)
Read Windows Server 2008 R2 Unleashed Online
Authors: Noel Morimoto

attacks and determine user passwords. If the PPP authentication exchange is encrypt-
ed, offline dictionary attacks are possible only after the encrypted packets have been
successfully decrypted.
Advantages of PPTP
Although L2TP/IPSec is more secure than a PPTP VPN session, there are significant reasons
organizations choose PPTP over L2TP/IPSec. The following are advantages of PPTP over
L2TP/IPSec:
. PPTP does not require a certificate infrastructure. L2TP/IPSec, SSTP, and DirectAccess
require a certificate infrastructure for issuing computer certificates to the VPN server
computer (or other authenticating server) and all VPN client computers.
. PPTP can be used by all Windows desktop platforms (Windows Server 2008,
Windows Server 2008 R2, Windows Server 2003, Windows 2000 Server, Windows 7,
874
CHAPTER 24
Server-to-Client Remote Access and DirectAccess
Windows Vista, Windows XP, Windows 2000 client, Windows NT 4.0, Windows
Millennium Edition [Me], Windows 98, and Windows 95 with the Windows Dial-Up
Networking 1.3 Performance and Security Update). Windows Server 2008 R2,
Windows Server 2008, Windows Server 2003, Windows 2000 Server, Windows 7,
Windows Vista, Windows XP, and Windows 2000 Workstation VPN clients are the
only clients that support L2TP/IPSec and the use of certificates. Windows 7 is the
only client that supports DirectAccess.
IPSec functions at a layer below the TCP/IP stack. This layer is controlled by a security
policy on each computer and a negotiated security association between the sender and
receiver. The policy consists of a set of filters and associated security behaviors. If a
packet’s IP address, protocol, and port number match a filter, the packet is subject to the
associated security behavior.
Advantages of SSTP
The SSTP protocol in Windows Server 2008 R2 gives administrators the capability to estab-
lish tunnels across the majority of corporate networks, bypassing many of the technical
hurdles that stop PPTP and L2TP.
The advantages of SSTP are as follows:
ptg
. SSTP helps lower administrative costs by reducing the technical steps needed to
tunnel between organizations. Because HTTPS is allowed through most firewalls and
proxy servers, there is no additional infrastructure changes needed to support SSTP.
. SSTP is certificate-based security implemented via SSL. However, certificates only
need to be issued to the servers rather than the clients. This provides the security
benefits of L2TP, but with almost the ease of configuration of PPTP.
The benefits are offset by the requirement that the client Certificate Authority require-
ments and the operating system requirement. The client requirement is that it trusts the
CA issuing the certificates and that it can access the certificate revocation list.
Support for SSTP in clients is available in Windows Server 2008, Windows Server 2008 R2,
Windows 7, Windows XP SP3 or later, and Windows Vista SP1 or later.
Advantages of DirectAccess
DirectAccess is a new technology introduced with Windows Server 2008 R2 and is a
completely new idea for remote access. Essentially, DirectAccess is a transparent always-on
remote access. It allows users to always appear to be on the corporate network and appear
as if they are in the office. In addition, it allows administrators to manage systems as local
systems through tools like Group Policy and Microsoft System Center Configuration
Manager (SCCM). From a user perspective, this is the easiest remote access solution. Once
configured, they don’t need to perform any action; it just works. From an administrator
point of view, however, this solution is the most complex due to the IPv6 and certificate
requirements.
Choosing Between Traditional VPN Technologies and DirectAccess
875
The advantages of DirectAccess are as follows:
. DirectAccess provides seamless connectivity wherever a remote system has an
Internet connection. No user interaction is required.
. System administrators can manage remotely connected systems as if they were inter-
nal systems.
24
. DirectAccess allows folder redirection so that all critical data is maintained inside the
corporate network and backed up using enterprise tools.
. DirectAccess uses a new technology, Name Resolution Policy Table (NRPT), to deter-
mine the appropriate DNS server for connection requests. Combined with split-tun-
neling, this makes for a truly transparent solution.
Despite these benefits, DirectAccess can be somewhat complex to implement. If most of
the pieces, such as IPv6, PKI, and Windows 7 on the desktop are already in place,
DirectAccess might be the best overall remote access solution for Windows Server 2008 R2.
NOTE
One advantage of DirectAccess is the fact that it uses IPv6. For organizations that have
been looking to deploy IPv6 and gain experience with this new addressing scheme, the
ptg
DirectAccess technology provides a good IPv6 learning platform that is self-contained
and integrates well with existing IPv4 technologies.
Ports Affecting the VPN Connectivity
Frequently, RRAS servers operating as VPN servers have two network cards, one of which is
plugged into the external network or DMZ. This is simpler, as there are typically few
restrictions on communicating with that externally facing interface. The RRAS server is
firewalled and the externally facing interface is hardened as a matter of best practice to
mitigate the potential risks. In fact, this is a requirement for DirectAccess servers.
However, even with mitigation steps, this externally facing interface can present an unac-
ceptable level of risk to some organizations. In those cases, the VPN infrastructure must
remain entirely within the internal network. In that configuration, the firewall must be
configured to allow the appropriate traffic to the RRAS server.
Table 24.3 and Table 24.4 list the relevant firewall rules needed for the PPTP and L2TP
protocols. The IP address for each of the rules is the RRAS server address, which is the
destination if the direction is inbound and the source if the direction is outbound.
TABLE 24.3
Firewall Rules for the RRAS Server for PPTP
Direction
Protocol
Port or
Why?
ID
Inbound
TCP
1723
Allows PPTP tunnel maintenance traffic from the PPTP client to
the PPTP server
876
CHAPTER 24
Server-to-Client Remote Access and DirectAccess
TABLE 24.3
Firewall Rules for the RRAS Server for PPTP
Direction
Protocol
Port or
Why?
ID
Inbound
IP
47
Allows tunneled PPTP data from the PPTP client to the PPTP
server
Outbound
TCP
1723
Allows PPTP tunnel maintenance traffic from the PPTP server to
the PPTP client
Outbound
IP
47
Allows tunneled PPTP data from the PPTP server to the PPTP
client
TABLE 24.4
Firewall Rules for the RRAS Server for L2TP
Direction Protocol Port or ID Why?
Inbound
UDP
500
Allows IKE traffic to the VPN server
Inbound
UDP
4500
Allows IPSec NAT-T traffic to the VPN server
Inbound
IP
50
Allows IPSec ESP traffic to the VPN server
Outbound UDP
500
Allows IKE traffic from the VPN server
ptg
Outbound UDP
4500
Allows IPSec NAT-T traffic from the VPN server
Outbound IP
50
Allows IPSec ESP traffic from the VPN server
NOTE
Interestingly, because the DirectAccess server must be a dual-homed server with a net-
work interface on the public network, there are no ports needed on the firewall for
DirectAccess. In effect, it bypasses the firewall completely.
The SSTP protocol is simple and only requires that TCP port 443 be permitted inbound to
the RRAS server.
The best way to illustrate the concepts in this chapter is to walk through a sample VPN
scenario. The example will walk through the setup and testing of a VPN infrastructure that
will include health checks and remediation of a client. The sample VPN scenario architec-
ture is shown in Figure 24.15.
The scenario will use the systems with the basic configuration shown in Table 24.5. These
examples assume that an Active Directory domain companyabc.com has been created and
that DC1 is the domain controller.
Traditional VPN Scenario
877
VISTA1
VPN Client
VPN1
192.168.1.201
24
RRAS Server
172.16.1.152
172.16.1.100
172.16.1.151
DC1
NPS1
Active Directory
Network Policy Server
Server
Certificate Server
FIGURE 24.15
VPN scenario diagram.
ptg
TABLE 24.5
VPN Scenario Servers
Server
Roles
Operating System
IP Address
DC1
Directory server
Windows Server 2008
172.16.1.100
R2
NPS1
Network Policy Server Certificate
Windows Server 2008
172.16.1.151
server
R2
VPN1
RRAS server
Windows Server 2008
172.16.1.152 (internal)
R2
192.168.1.201 (external)
VISTA1
VPN client
Windows Vista SP1
The steps to configure the VPN architecture will consist of the following:
. Set up the certificate server.
. Set up the Network Policy Server.
. Configure the Network Policy Server.
. Set up the RRAS.
. Set up the VPN client.
. Test the VPN connection.
. Control unhealthy VPN clients.
878
CHAPTER 24
Server-to-Client Remote Access and DirectAccess
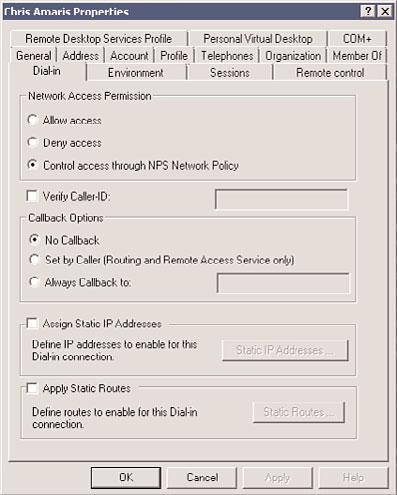
In Windows Server 2008 R2 Active Directory, the users would need to be enabled in the
Dial-in tab of the account properties. As you can see in Figure 24.16, the default option is
Control Access Through NPS Network Policy.
ptg
FIGURE 24.16
Dial-in tab in Windows Server 2008 R2 Active Directory.
We’ll now step through the setup, configuration, and testing of a Windows Server 2008 R2
traditional VPN infrastructure.
Setting Up the Certificate Server
The first step is to configure the certificate server. This server will be used to issue certifi-
cates for the VPN infrastructure. The example uses Microsoft Certificate Services, but a
third-party CA and certificates could be used as well.
The NPS1 server was chosen for this example, as it will be the centralized policy server
and so is well situated to provide certificate services. A completely separate server could
have been configured as well. The procedure assumes that the Windows Server 2008 R2
operating system has been installed and that the NPS1 server has joined the compa-
nyabc.com domain.
Install the Active Directory Certificate Services role on the NPS1 server using the following
steps:
1. Launch Server Manager.
2. In the Roles Summary pane, select Add Roles to start the wizard.
Traditional VPN Scenario
879
3. Click Next.
4. Select Active Directory Certificate Services, and click Next.
5. Click Next.
6. Check the Certification Authority Web Enrollment to add the check mark.
7. A window opens with an additional set of role services and features required to
24
support web enrollment. Click Add Required Role Services to add these prerequisites.
8. Click Next.
9. Leave the Enterprise option to create an enterprise CA, and click Next.
10. Leave the Root CA option selected, and click Next.
11. Leave the Create a New Private Key option selected, and click Next.
12. Click Next to accept the cryptography options for the CA.
13. Click Next to accept the CA name.
14. Click Next to accept the default validity period of five years.
15. Click Next to accept the default directories.
16. Click Next.
17. Click Next to accept the default web server role services.
ptg
18. Click Install to install the roles.
