A Government of Wolves: The Emerging American Police State (20 page)
Read A Government of Wolves: The Emerging American Police State Online
Authors: John W. Whitehead

Some DHS officials at the various fusion centers throughout the country received no more than five days of training in intelligence gathering. Despite this, they were being paid upwards of $80,000 a year. This lack of adequate training may help explain why innocent, constitutionally protected activities have been flagged as potentially terrorist in nature. For example, one intelligence report warned against a "Russian cyberattack," which turned out to be nothing more than an American employee accessing a work computer remotely.
347
Unfortunately, the liberal application of the phrase "suspicious activity" has allowed fusion centers and intelligence agents to label pretty much any activity as a potential terror threat. The idea is to track "suspicious" individuals who are performing innocent activities which may add up to something more sinister. More often than not, however, the result is just a lot of dead ends. For example, of the 386 unclassified fusion center homeland intelligence reports reviewed by the Senate Permanent Subcommittee, "close to 300 of them had no discernible connection to terrorists, terrorist plots, or threats."
348
Then again, you're bound to end up with few legitimate leads on "terrorist" activity if you classify unemployment as a cause for suspicion, which is actually one of the criteria used by TLOs.
349
The problem with tracking innocent behavior is that more often than not innocent people will be investigated for heinous crimes. For example, in 2007 a police officer filed a report on a man who had been seen purchasing "large quantities of liquid chlorine bleach and ammonia" on consecutive days. When that information traveled to the fusion center, it was picked out as a "suspicious activity" and the individual was investigated. It turned out that the man was a golf course owner attempting to circumvent a ban on gopher traps by killing the rodents with chlorine gas.
350
Among the many groups of innocent people labeled suspicious and targeted for surveillance are pro-choice advocates, pro-life advocates, environmental activists, Tea Party members, Second Amendment rally attendees, third-party voters, Ron Paul supporters, anti-death penalty advocates, and antiwar activists.
351
According to a fusion center in Virginia, universities and religious institutions are potential hubs of extremism and terrorist activity. Another fusion center specifically cited historically black and Christian evangelical colleges as cause for concern.
352
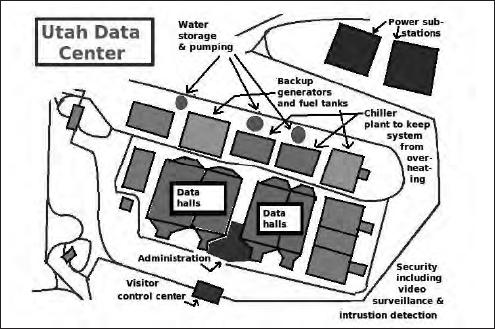
NSA Data Center in Bluffdale
America's Crown Jewel
Even with the preponderance of fusion centers and their poor track records, the government continues to push for more access, more control, and more surveillance of American citizens. The Utah Data Center (UDC), a $2 billion behemoth that houses a network of computers, satellites, and phone lines that stretches across the world,
353
serves as the crown jewel of the federal government's surveillance empire.
Situated in the small desert town of Bluffdale, Utah, not far from bustling Salt Lake City, the UDC is the central hub of the National Security Agency's (NSA) vast spying infrastructure. At five times the size of the U.S. Capitol,
354
the UDC is a clearinghouse and a depository for every imaginable kind of information
355
to be tracked, collected, catalogued, and analyzed by the UDC's supercomputers and its teams of government agents. In this way, by sifting through the detritus of your once-private life, the government will come to its own conclusions about who you are, where you fit in, and how best to deal with you should the need arise.
356
What little we know about this highly classified spy center and its parent agency, the NSA, comes from James Bamford, a former intelligence analyst and an expert on the highly secretive government agency. Bamford provides a chilling glimpse into the government's plans for total control, a.k.a., total information awareness. As Bamford notes, the NSA "has transformed itself into the largest, most covert, and potentially most intrusive intelligence agency ever created. In the process–and for the first time since Watergate and the other scandals of the Nixon administration–the NSA has turned its surveillance apparatus on the United States and its citizens."
357
Supposedly created by the NSA in order to track foreign threats to America, as well as to shore up cybersecurity and battle hackers,
358
the UDC's technological capabilities are astounding. As the central depository for all of the information gathered by the NSAs vast spy centers, the UDC's supercomputers can download data amounting to the entire contents of the Library of Congress
every six hours
. However, the data targeted goes far beyond the scope of terrorist threats. In fact, as Bamford points out, the NSA is interested in nothing less than the "so-called invisible web, also known as the deep web or deepnet–data beyond the reach of the public. This includes password-protected data, U.S. and foreign government communications, and noncommercial file-sharing between trusted peers."
359
Everybody's a Target
That the NSA, which has shown itself to care little for constitutional limits or privacy, is the driving force behind this spy center is no surprise. The agency–which is three times the size of the CIA, consumes one third of the intelligence budget and has a global spy network
360
–has a long history of spying on Americans, whether or not it has always had the authorization to do so. Take, for instance, the warrantless wiretapping program conducted during the George W. Bush years,
361
which resulted in the NSA monitoring the private communications of millions of Americans–a program that continues unabated today–with help from private telecommunications companies such as AT&T. The program recorded 320 million phone calls
a day
when it first started.
362
It is estimated that the NSA has intercepted at least 20 trillion communications by American citizens since 9/11.
363
Clearly, the age of privacy in America is coming to a close. We have moved into a new paradigm in which surveillance technology that renders everyone a suspect is driving the bureaucratic ship that once was our democratic republic. We are all becoming data collected in government files. As a senior intelligence official previously involved with the National Security Agency's Utah Data Center remarked, "Everybody's a target; everybody with communication is a target."
364
The author and dissident Aleksandr Solzhenitsyn, who suffered under the secret police in the Soviet Union, wrote about this process some years ago:
As every man goes through life he fills in a number of forms for the record, each containing a number of questions... There are thus hundreds of little threads radiating from every man, millions of threads in all. If these threads were suddenly to become visible, the whole sky would look like a spider's web, and if they materialized like rubber bands, buses and trams and even people would lose the ability to move and the wind would be unable to carry torn-up newspapers or autumn leaves along the streets of the city.
365
The privacy and dignity of our citizens [are] being whittled away by sometimes imperceptible steps. Taken individually, each step may be of little consequence. But when viewed as a whole, there begins to emerge a society quite unlike any we have seen –a society in which government may intrude into the secret regions of a [person's] life."
366
–Former U.S. Supreme Courtjustice WILLIAM O. DOUGLAS
T
he obvious goal of the corporate state, of course, is to create a total control society–one in which the government is able to track the movements of people in real time and control who does what, when, and where. This is accomplished through mass surveillance, sold to the American people by way of the two highly manipulative, siren-song catchwords of our modern age–security and convenience.
Surveillance once relied primarily on government or corporate agents peering through binoculars, listening to conversations through a bugged telephone, or actively monitoring a camera. However, the government's mass surveillance tools are many and growing. This includes, at a bare minimum, surveillance cameras, electronic eavesdropping devices, traffic cameras, biometrics, radio-frequency identification cards, and satellites, all of which persistently monitor the behaviors and actions of the public while intruding on one's privacy.
Technology is on the march and there are virtually no limitations to its uses against American citizens. The U.S. government and its corporate allies are looking out for you–literally–with surveillance tools intended to identify you, track your whereabouts, monitor your activities and allow or restrict your access to people, places, or things deemed suitable by the government.
Surveillance Cameras
As of 2007 there were approximately 30 million surveillance cameras located throughout the United States. At that time, the average American was captured on film by a surveillance camera more than 200 times a day.
367
Thus, surrounded at every turn by surveillance cameras in one form or another on street corners, at the ATM, at convenience stores, and even in public restrooms, Americans have proven to be relatively adaptable to life in a goldfish bowl.
Indeed, surveillance cameras, which operate in real time, and can be seen perched on traffic lights, alongside highways and roads, on bridges, expressways, and even on school buses, are perhaps the perfect example of how easy it was for the government to lead us down that slippery slope into a surveillance state. Sold to the public as safety devices to monitor traffic jams, catch drivers who break the law by speeding or perhaps running a red light, these cameras–often operated by private corporations–are little more than surveillance and revenue-raising devices for corporations, states, and municipalities, which use them to levy fines against alleged lawbreakers.
368
Yet when coupled with license-plate readers, mobile scanners, and iris scanners to full-body scanners in airports, biometrie ID cards, etc., they become yet another layer in our surveillance society.
Mobile Scanners
There is no limit to what these technological gadgets can do in the so-called name of efficiency, expediency, economy, and security. For example, law enforcement agencies now have license-plate recognition scanners that can sweep a parking lot full of cars in under a minute and check them against police databases. "Police like the devices for their speed and efficiency but mostly for their ability to record thousands of plates and their locations each day," writes journalist Christine Vendei. "The information is loaded wirelessly into a police database and archived for possible searches later."
369
With such a tool at its disposal, the government can retroactively pinpoint exactly where you were on any given day. And if you have the bad luck of being in the wrong place at the wrong time, the burden of proving your innocence will rest with you.
For some years now, Americans have been conditioned to full-body scans and invasive pat downs at airports. Now a mobile version of an airport full-body scanner is already roaming some of America's streets and neighborhoods. Mounted in nondescript delivery vehicles that enable police or other government agents to blend into urban and other landscapes, these roving x-ray scanners "bounce a narrow stream of x-rays off and through nearby objects, and read which ones come back," thereby producing instantaneous photo-like images of whatever the van passes– whether cars, trucks, containers, homes, or people.
370
In other words, the government can now do drive-by strip searches of your person and your home, including monitoring what you are doing in the privacy of your home. Even though you may be innocent of any wrongdoing whatsoever,
every
aspect of your life, as well as
every
room of your house and
everything
you do in your house, will be under scrutiny by government agents–and can and will be recorded and used against you at a later date.
