The Code Book (15 page)

This distribution is harder to analyze. There are no obvious candidates for the three neighboring peaks that correspond to R-S -T. However, the depression that stretches from G to L is very distinct, and probably corresponds to the depression we expect to see stretching from U to Z in the standard distribution. If this were the case, we would expect the three R-S-T peaks to appear at D, E and F, but the peak at E is missing. For the time being, we shall dismiss the missing peak as a statistical glitch, and go with our initial reaction, which is that the depression from G to L is a recognizably shifted feature. This would suggest that all the letters encrypted according to L
2
have been shifted twelve places, or that L
2
defines a cipher alphabet which begins M, N, O, P,… and that the second letter of the keyword, L
2
, is M. Once again, this hypothesis can be tested by shifting the L
2
distribution back twelve letters and comparing it with the standard distribution.
Figure 18
shows both distributions, and the match between the major peaks is very strong, implying that it is safe to assume that the second letter of the keyword is indeed M.
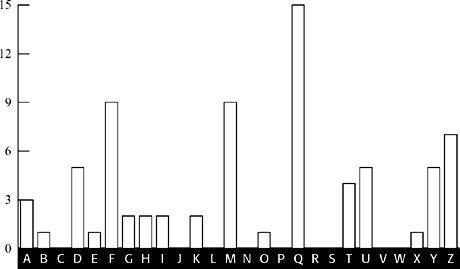
Figure 17
Frequency distribution for letters in the ciphertext encrypted using the L
2
cipher alphabet (number of occurrences).
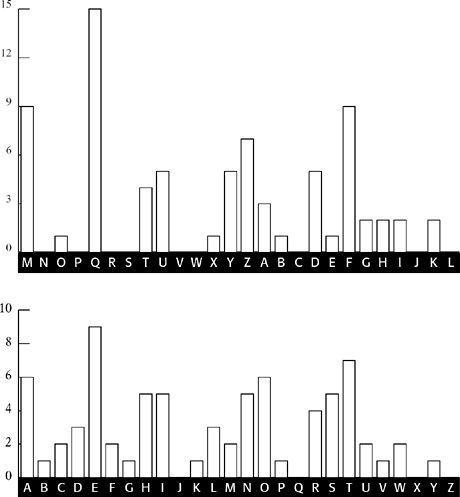
Figure 18
The L
2
distribution shifted back twelve letters (top), compared with the standard frequency distribution (bottom). Most major peaks and troughs match.
I shall not continue the analysis; suffice to say that analyzing the 3rd, 8th, 13th, … letters implies that the third letter of the keyword is I, analyzing the 4th, 9th, 14th, … letters implies that the fourth letter is L, and analyzing the 5th, 10th, 15th, … letters implies that the fifth letter is Y. The keyword is EMILY. It is now possible to reverse the Vigenère cipher and complete the cryptanalysis. The first letter of the ciphertext is W, and it was encrypted according to the first letter of the keyword, E. Working backward, we look at the Vigenère square, and find W in the row beginning with E, and then we find which letter is at the top of that column. The letter is s, which must make it the first letter of the plaintext. By repeating this process, we see that the plaintext begins sittheedownandhavenoshamecheekbyjowl.… By inserting suitable word-breaks and punctuation, we eventually get:
Sit thee down, and have no shame,
Cheek by jowl, and knee by knee:
What care I for any name?
What for order or degree?
Let me screw thee up a peg:
Let me loose thy tongue with wine:
Callest thou that thing a leg?
Which is thinnest? thine or mine?
Thou shalt not be saved by works:
Thou hast been a sinner too:
Ruined trunks on withered forks,
Empty scarecrows, I and you!
Fill the cup, and fill the can:
Have a rouse before the morn:
Every moment dies a man,
Every moment one is born.
These are verses from a poem by Alfred Tennyson entitled “The Vision of Sin.” The keyword happens to be the first name of Tennyson’s wife, Emily Sellwood. I chose to use a section from this particular poem as an example for cryptanalysis because it inspired some curious correspondence between Babbage and the great poet. Being a keen statistician and compiler of mortality tables, Babbage was irritated by the lines “Every moment dies a man, Every moment one is born,” which are the last lines of the plaintext above. Consequently, he offered a correction to Tennyson’s “otherwise beautiful” poem:
It must be manifest that if this were true, the population of the world would be at a standstill … I would suggest that in the next edition of your poem you have it read—“Every moment dies a man, Every moment 1is born.” … The actual figure is so long I cannot get it onto a line, but I believe the figure 1
will be sufficiently accurate for poetry.
I am, Sir, yours, etc.,
Charles Babbage.
Babbage’s successful cryptanalysis of the Vigenère cipher was probably achieved in 1854, soon after his spat with Thwaites, but his discovery went completely unrecognized because he never published it. The discovery came to light only in the twentieth century, when scholars examined Babbage’s extensive notes. In the meantime, his technique was independently discovered by Friedrich Wilhelm Kasiski, a retired officer in the Prussian army. Ever since 1863, when he published his cryptanalytic breakthrough in
Die Geheimschriften und die Dechiffrir-kunst
(“Secret Writing and the Art of Deciphering”), the technique has been known as the Kasiski Test, and Babbage’s contribution has been largely ignored.
And why did Babbage fail to publicize his cracking of such a vital cipher? He certainly had a habit of not finishing projects and not publishing his discoveries, which might suggest that this is just one more example of his lackadaisical attitude. However, there is an alternative explanation. His discovery occurred soon after the outbreak of the Crimean War, and one theory is that it gave the British a clear advantage over their Russian enemy. It is quite possible that British Intelligence demanded that Babbage keep his work secret, thus providing them with a nine-year head start over the rest of the world. If this was the case, then it would fit in with the long-standing tradition of hushing up codebreaking achievements in the interests of national security, a practice that has continued into the twentieth century.
From Agony Columns to Buried Treasure
Thanks to the breakthroughs by Charles Babbage and Friedrich Kasiski, the Vigenère cipher was no longer secure. Cryptographers could no longer guarantee secrecy, now that cryptanalysts had fought back to regain control in the communications war. Although cryptographers attempted to design new ciphers, nothing of great significance emerged during the latter half of the nineteenth century, and professional cryptography was in disarray. However, this same period witnessed an enormous growth of interest in ciphers among the general public.
The development of the telegraph, which had driven a commercial interest in cryptography, was also responsible for generating public interest in cryptography. The public became aware of the need to protect personal messages of a highly sensitive nature, and if necessary they would use encryption, even though this took more time to send, thus adding to the cost of the telegram. Morse operators could send plain English at speeds of up to 35 words per minute because they could memorize entire phrases and transmit them in a single burst, whereas the jumble of letters that make up a ciphertext was considerably slower to transmit, because the operator had to continually refer back to the sender’s written message to check the sequence of letters. The ciphers used by the general public would not have withstood attack by a professional cryptanalyst, but they were sufficient to guard against the casual snooper.
As people became comfortable with encipherment, they began to express their cryptographic skills in a variety of ways. For example, young lovers in Victorian England were often forbidden from publicly expressing their affection, and could not even communicate by letter in case their parents intercepted and read the contents. This resulted in lovers sending encrypted messages to each other via the personal columns of newspapers. These “agony columns,” as they became known, provoked the curiosity of cryptanalysts, who would scan the notes and try to decipher their titillating contents. Charles Babbage is known to have indulged in this activity, along with his friends Sir Charles Wheatstone and Baron Lyon Playfair, who together were responsible for developing the deft
Playfair cipher
(described in
Appendix E
). On one occasion, Wheatstone deciphered a note in
The Times
from an Oxford student, suggesting to his true love that they elope. A few days later, Wheatstone inserted his own message, encrypted in the same cipher, advising the couple against this rebellious and rash action. Shortly afterward there appeared a third message, this time unencrypted and from the lady in question: “Dear Charlie, Write no more. Our cipher is discovered.”
In due course a wider variety of encrypted notes appeared in the newspapers. Cryptographers began to insert blocks of ciphertext merely to challenge their colleagues. On other occasions, encrypted notes were used to criticize public figures or organizations.
The Times
once unwittingly carried the following encrypted notice:
“The Times
is the Jeffreys of the press.” The newspaper was being likened to the notorious seventeenth-century Judge Jeffreys, implying that it was a ruthless, bullying publication which acted as a mouthpiece for the government.
Another example of the public’s familiarity with cryptography was the widespread use of pinprick encryption. The ancient Greek historian Aeneas the Tactician suggested conveying a secret message by pricking tiny holes under particular letters in an apparently innocuous page of text, just as there are dots under some letters in this paragraph. Those letters would spell out a secret message, easily read by the intended receiver. However, if an intermediary stared at the page, they would probably be oblivious to the barely perceptible pinpricks, and would probably be unaware of the secret message. Two thousand years later, British letter writers used exactly the same method, not to achieve secrecy but to avoid paying excessive postage costs. Before the overhaul of the postage system in the mid-1800s, sending a letter cost about a shilling for every hundred miles, beyond the means of most people. However, newspapers could be posted free of charge, and this provided a loophole for thrifty Victorians. Instead of writing and sending letters, people began to use pinpricks to spell out a message on the front page of a newspaper. They could then send the newspaper through the post without having to pay a penny.
The public’s growing fascination with cryptographic techniques meant that codes and ciphers soon found their way into nineteenth-century literature. In Jules Verne’s
Journey to the Center of the Earth
, the decipherment of a parchment filled with runic characters prompts the first step on the epic journey. The characters are part of a substitution cipher which generates a Latin script, which in turn makes sense only when the letters are reversed: “Descend the crater of the volcano of Sneffels when the shadow of Scartaris comes to caress it before the calends of July, audacious voyager, and you will reach the center of the Earth.” In 1885, Verne also used a cipher as a pivotal element in his novel
Mathias Sandorff
. In Britain, one of the finest writers of cryptographic fiction was Sir Arthur Conan Doyle. Not surprisingly, Sherlock Holmes was an expert in cryptography and, as he explained to Dr. Watson, was “the author of a trifling monograph upon the subject in which I analyze one hundred and sixty separate ciphers.” The most famous of Holmes’s decipherments is told in
The Adventure of the Dancing Men
, which involves a cipher consisting of stick-men, each pose representing a distinct letter.
