The Code Book (18 page)

Despite the combined efforts of the Association, amateur treasure hunters and professional cryptanalysts, the first and third Beale ciphers have remained a mystery for over a century, and the gold, silver and jewels have yet to be found. Many attempts at decipherment have revolved around the Declaration of Independence, which was the key for the second Beale cipher. Although a straightforward numbering of the words of the Declaration yields nothing useful for the first and third ciphers, cryptanalysts have tried various other schemes, such as numbering it backward or numbering alternate words, but so far nothing has worked. One problem is that the first cipher contains numbers as high as 2906, whereas the Declaration contains only 1,322 words. Other texts and books have been considered as potential keys, and many cryptanalysts have looked into the possibility of an entirely different encryption system.
You might be surprised by the strength of the unbroken Beale ciphers, especially bearing in mind that when we left the ongoing battle between codemakers and codebreakers, it was the codebreakers who were on top. Babbage and Kasiski had invented a way of breaking the Vigenère cipher, and codemakers were struggling to find something to replace it. How did Beale come up with something that is so formidable? The answer is that the Beale ciphers were created under circumstances that gave the cryptographer a great advantage. This matter concerns just three messages, and, because they related to such a valuable treasure, Beale might have been prepared to create a special keytext for the first and third ciphers. Indeed, if the keytext was penned by Beale himself, this would explain why searches of published material have not revealed it. We can imagine that Beale might have written a 2,000-word private essay on the subject of buffalo hunting, of which there was only one copy. Only the holder of this essay, the unique keytext, would be able to decipher the first and third Beale ciphers. Beale mentioned that he had left the key in “the hand of a friend” in St. Louis, but if the friend lost or destroyed the key, then cryptanalysts might never be able to crack the Beale ciphers.
Creating a keytext for a message is much more secure than using a key based on a published book, but it is practical only if the sender has the time to create the keytext and is able to convey it to the intended recipient, requirements that are not feasible for routine, day-to-day communications. In Beale’s case, he could compose his keytext at leisure, deliver it to his friend in St. Louis whenever he happened to be passing through, and then have it posted or collected at some arbitrary time in the future, whenever the treasure was to be reclaimed.
An alternative theory for explaining the indecipherability of the Beale ciphers is that the author of the pamphlet deliberately sabotaged them before having them published. Perhaps the author merely wanted to flush out the key, which was apparently in the hands of Beale’s friend in St. Louis. If he had accurately published the ciphers, then the friend would have been able to decipher them and collect the gold, and the author would have received no reward for his efforts. However, if the ciphers were corrupted in some way, then the friend would eventually realize that he needed the author’s help, and would contact the publisher, Ward, who in turn would contact the author. The author could then hand over the accurate ciphers in exchange for a share of the treasure.
It is also possible that the treasure was found many years ago, and that the discoverer spirited it away without being spotted by local residents. Beale enthusiasts with a penchant for conspiracy theories have suggested that the National Security Agency (NSA) has already found the treasure. America’s central government cipher facility has access to the most powerful computers and some of the most brilliant minds in the world, and they may have discovered something about the ciphers that has eluded everybody else. The lack of any announcement would be in keeping with the NSA’s hush-hush reputation—it has been proposed that NSA does not stand for National Security Agency, but rather “Never Say Anything” or “No Such Agency.”
Finally, we cannot exclude the possibility that the Beale ciphers are an elaborate hoax, and that Beale never existed. Sceptics have suggested that the unknown author, inspired by Poe’s “The Gold Bug,” fabricated the whole story and published the pamphlet as a way of profiting from the greed of others. Supporters of the hoax theory have searched for inconsistencies and flaws in the Beale story. For example, according to the pamphlet, Beale’s letter, which was locked in the iron box and supposedly written in 1822, contains the word “stampede,” but this word was not seen in print until 1834. However, it is quite possible that the word was in common use in the Wild West at a much earlier date, and Beale could have learned of it on his travels.
One of the foremost nonbelievers is the cryptographer Louis Kruh, who claims to have found evidence that the pamphlet’s author also wrote Beale’s letters, the one supposedly sent from St. Louis and the one supposedly contained in the box. He performed a textual analysis on the words attributed to the author and the words attributed to Beale to see if there were any similarities. Kruh compared aspects such as the percentage of sentences beginning with “The,” “Of” and “And,” the average number of commas and semicolons per sentence, and the writing style—the use of negatives, negative passives, infinitives, relative clauses, and so on. In addition to the author’s words and Beale’s letters, the analysis also took in the writing of three other nineteenth-century Virginians. Of the five sets of writing, those authored by Beale and the pamphlet’s author bore the closest resemblance, suggesting that they may have been written by the same person. In other words, this suggests that the author faked the letters attributed to Beale and fabricated the whole story.
On the other hand, evidence for the integrity of the Beale ciphers is provided from various sources. First, if the undeciphered ciphers were hoaxes, we might expect the hoaxer to have chosen the numbers with little or no attention. However, the numbers give rise to various intricate patterns. One of the patterns can be found by using the Declaration of Independence as a key for the first cipher. This yields no discernible words, but it does give sequences such as abfdefghiijklmmnohpp. Although this is not a perfect alphabetical list, it is certainly not random. James Gillogly of the American Cryptogram Association is not convinced that the Beale ciphers are authentic. However, he estimates that the probability of such sequences appearing by chance is less than one in a hundred million million, suggesting that there is a cryptographic principle underlying the first cipher. One theory is that the Declaration is indeed the key, but the resulting text requires a second stage of decipherment; in other words, the first Beale cipher was enciphered by a two-stage process, so-called superencipherment. If this is so, then the alphabetical sequence might have been put there as a sign of encouragement, a hint that the first stage of decipherment has been successfully completed.
Further evidence favoring the probity of the ciphers comes from historical research, which can be used to verify the story of Thomas Beale. Peter Viemeister, a local historian, has gathered much of the research in his book
The Beale Treasure–History of a Mystery
. Viemeister began by asking if there was any evidence that Thomas Beale actually existed. Using the census of 1790 and other documents, Viemeister has identified several Thomas Beales who were born in Virginia and whose backgrounds fit the few known details. Viemeister has also attempted to corroborate the other details in the pamphlet, such as Beale’s trip to Santa Fe and his discovery of gold. For example, there is a Cheyenne legend dating from around 1820 which tells of gold and silver being taken from the West and buried in Eastern Mountains. Also, the 1820 postmaster’s list in St. Louis contains a “Thomas Beall,” which fits in with the pamphlet’s claim that Beale passed through the city in 1820 on his journey westward after leaving Lynchburg. The pamphlet also says that Beale sent a letter from St. Louis in 1822.
So there does seem to be a basis for the tale of the Beale ciphers, and consequently it continues to enthrall cryptanalysts and treasure hunters, such as Joseph Jancik, Marilyn Parsons and their dog Muffin. In February 1983 they were charged with “violation of a sepulcher,” after being caught digging in the cemetery of Mountain View Church in the middle of the night. Having discovered nothing other than a coffin, they spent the rest of the weekend in the county jail and were eventually fined $500. These amateur gravediggers can console themselves with the knowledge that they were hardly any less successful than Mel Fisher, the professional treasure hunter who salvaged $40 million worth of gold from the sunken Spanish galleon
Nuestra Señora de Atocha
, which he discovered off Key West, Florida, in 1985. In November 1989, Fisher received a tip-off from a Beale expert in Florida, who believed that Beale’s hoard was buried at Graham’s Mill in Bedford County, Virginia. Supported by a team of wealthy investors, Fisher bought the site under the name of Mr. Voda, in order to avoid arousing any suspicion. Despite a lengthy excavation, he discovered nothing.
Some treasure hunters have abandoned hope of cracking the two undeciphered sheets, and have concentrated instead on gleaning clues from the one cipher that has been deciphered. For example, as well as describing the contents of the buried treasure, the solved cipher states that it is deposited “about four miles from Buford’s,” which probably refers to the community of Buford or, more specifically, to Buford’s Tavern, located at the center of
Figure 25
. The cipher also mentions that “the vault is roughly lined with stone,” so many treasure hunters have searched along Goose Creek, a rich source of large stones. Each summer the region attracts hopefuls, some armed with metal detectors, others accompanied by psychics or diviners. The nearby town of Bedford has a number of businesses which gladly hire out equipment, including industrial diggers. Local farmers tend to be less welcoming to the strangers, who often trespass on their land, damage their fences and dig giant holes.
Having read the tale of the Beale ciphers, you might be encouraged to take up the challenge yourself. The lure of an unbroken nineteenth-century cipher, together with a treasure worth $20 million, might prove irresistible. However, before you set off on the treasure trail, take heed of the advice given by the author of the pamphlet:
Before giving the papers to the public, I would say a word to those who may take an interest in them, and give them a little advice, acquired by bitter experience. It is, to devote only such time as can be spared from your legitimate business to the task, and if you can spare no time, let the matter alone … Again, never, as I have done, sacrifice your own and your family’s interests to what may prove an illusion; but, as I have already said, when your day’s work is done, and you are comfortably seated by your good fire, a short time devoted to the subject can injure no one, and may bring its reward.
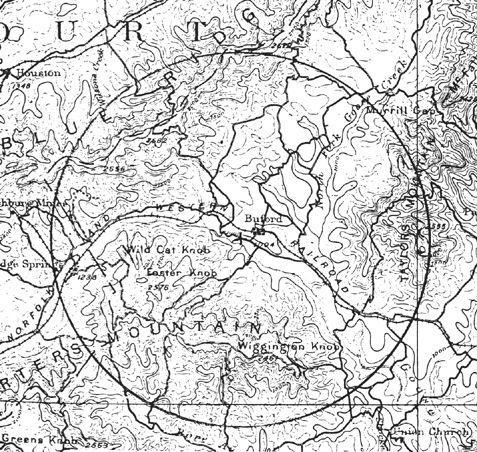
Figure 25
Part of a U.S. Geological Survey map of 1891. The circle has a radius of four miles, and is centered on Buford’s Tavern, a location alluded to in the second cipher.
3 The Mechanization of Secrecy
A
t the end of the nineteenth century, cryptography was in disarray. Ever since Babbage and Kasiski had destroyed the security of the Vigenère cipher, cryptographers had been searching for a new cipher, something that would reestablish secret communication, thereby allowing businessmen and the military to exploit the immediacy of the telegraph without their communications being stolen and deciphered. Furthermore, at the turn of the century, the Italian physicist Guglielmo Marconi invented an even more powerful form of telecommunication, which made the need for secure encryption even more pressing.
In 1894, Marconi began experimenting with a curious property of electrical circuits. Under certain conditions, if one circuit carried an electric current, this could induce a current in another isolated circuit some distance away. By enhancing the design of the two circuits, increasing the power and adding aerials, Marconi could soon transmit and receive pulses of information across distances of up to 2.5 km. He had invented radio. The telegraph had already been established for half a century, but it required a wire to transport a message between sender and receiver. Marconi’s system had the great advantage of being wireless—the signal traveled, as if by magic, through the air.
In 1896, in search of financial backing for his idea, Marconi emigrated to Britain, where he filed his first patent. Continuing his experiments, he increased the range of his radio communications, first transmitting a message 15 km across the Bristol Channel, and then 53 km across the English Channel to France. At the same time he began to look for commercial applications for his invention, pointing out to potential backers the two main advantages of radio: it did not require the construction of expensive telegraph lines, and it had the potential to send messages between otherwise isolated locations. He pulled off a magnificent publicity stunt in 1899, when he equipped two ships with radios so that journalists covering the America’s Cup, the world’s most important yacht race, could send reports back to New York for the following day’s newspapers.
