Windows Server 2008 R2 Unleashed (35 page)
Read Windows Server 2008 R2 Unleashed Online
Authors: Noel Morimoto

133
mized by being stored in the application partition, thus reducing replication traffic and
improving performance. For more information on DNS, see Chapter 9, “Integrating Active
Directory in a UNIX Environment.”
Understanding How AD DS DNS Works with Foreign DNS
Often, some local administrators might be hesitant to deploy AD DS because of their
desire to maintain their own foreign DNS implementation, usually UNIX BIND. If this is
the case, it is possible for Windows Server 2008 R2 DNS to coexist in this type of environ-
ment, as long as the DNS supports dynamic updates and SRV records (BIND 8.2.x or
higher). These situations occur more often than not, as political situations within IT
departments are often divided into pro-Microsoft and pro-UNIX groups, each of which has
its own ideology and plans. The ability of Windows Server 2008 R2 to coexist peacefully in
these types of environments is, therefore, key.
4
For a more detailed analysis of DNS in Windows Server 2008 R2, see Chapter 9.
ptg
The security built around Active Directory was designed to protect valuable network
assets. Development of Windows Server 2008 R2 security has also been affected by the
Trustworthy Computing initiative by Microsoft, which changed the primary focus of
Microsoft products to security. In a nutshell, Microsoft is more focused than ever before
on the security of its products, and all new features must pass a security litmus test before
they can be released. This initiative has affected the development of Windows Server 2008
R2 and is evident in the security features.
Understanding Kerberos Authentication
Kerberos was originally designed at MIT as a secure method of authenticating users
without actually sending a user password across the network, encrypted or not. Being able
to send a password this way greatly reduces the threat of password theft because malicious
users are no longer able to seize a copy of the password as it crosses the network and run
brute-force attacks on the information to decrypt it.
The actual functionality of Kerberos is complicated, but essentially what happens is the
computer sends an information packet to the client that requires authentication. This
packet contains a “riddle” of sorts that can be answered only by the user’s proper creden-
tials. The user applies the “answer” to the riddle and sends it back to the server. If the
proper password was applied to the answer, the user is authenticated. Although used in
Windows Server 2008 R2, this form of authentication is not proprietary to Microsoft, and
is available as an Internet standard. For a greater understanding of Kerberos security, see
Chapter 13, “Server-Level Security.”
134
CHAPTER 4
Active Directory Domain Services Primer
Taking Additional Security Precautions
AD DS implementations are, in essence, as secure as the Windows Server 2008 R2 environ-
ment in which they run. The security of the AD DS structure can be increased through the
utilization of additional security precautions, such as secured server-to-server communica-
tions using IPSec or the use of smart cards or other encryption techniques. In addition, the
user environment can be secured through the use of group policies that can set parameter
changes such as user password restrictions, domain security, and logon access privileges.
Outlining AD DS Changes in Windows Server 2008 R2
Improvements in the functionality and reliability of AD DS are of key importance to the
development team at Microsoft. It is, therefore, no small surprise that Windows Server
2008 R2 introduces improvements in AD DS. From the ability to have multiple password
policies in a domain to improvements in domain controller deployment with the RODC
role, the changes made to the structure of AD DS warrant a closer look.
Windows Server 2008 itself introduced multiple changes to AD DS functionality above
and beyond the Windows Server 2003 and Windows Server 2003 R2 Active Directory
versions. Windows Server 2008 R2 then introduced additional features and functionalities
above those introduced with the RTM version of Windows Server 2008. The Windows
ptg
Server 2008 R2 enhancements include the following:
.
Active Directory Recycle Bin—
Provides for the ability to restore deleted AD DS
objects
.
Offline Domain Join—
Allows for prestaging of the act of joining a workstation to
the AD DS domain
.
Managed Service Accounts—
Provides a mechanism for controlling and managing
AD DS service accounts
.
Authentication Mechanism Assurance—
Allows for administrators to grant access
to resources differently based on whether a user logs on with a smart card or multi-
factor authentication source or whether they log on via traditional techniques
.
Enhanced Administrative Tools—
Includes newly designed and powerful utilities
such as Active Directory Web Services, Active Directory Administrative Center, Active
Directory Best Practice Analyzer, a new AD DS Management Pack, and an Active
Directory Module for Windows PowerShell
The previous version of AD DS introduced with the release of Windows Server 2008
included the following key features that are still available with Windows Server 2008 R2. If
upgrading from any of the Windows Server 2003 versions of Active Directory or Windows
2000 Active Directory, all of these new features will be made available:
.
Ability to create multiple fine-grained password policies per domain—
Lifts
the restrictions of a single password policy per domain
.
Ability to restart AD DS on a domain controller—
Allows for maintenance of an
AD DS database without shutting the machine down
Outlining AD DS Changes in Windows Server 2008 R2
135
.
Enhanced AD DS auditing capabilities—
Provides useful and detailed item-level
auditing capabilities in AD DS without an overwhelming number of logs generated
Restoring Deleted AD DS Objects Using the Active Directory Recycle Bin
One of the most significant additions to Windows Server 2008 R2’s implementation of AD
DS is the Active Directory Recycle Bin. A Windows Server 2008 R2 Active Directory forest
and domain now allows for the recovery of deleted OUs, users, groups, or other AD
objects. There are a few prerequisites that must be satisfied, however, before the AD
Recycle Bin can be enabled:
. The AD DS forest and domain must be in Windows Server 2008 R2 functional level.
. When restoring objects, the OU in which they previously existed must first be
4
restored. If the object resided in a nested OU structure, the top-level OU must first
be restored, followed by the next-highest child OU, and so on.
. Membership in the Enterprise Administrators group is required to enable the AD
Recycle Bin.
. The process of enabling the AD Recycle Bin is nonreversible.
ptg
Enabling the AD Recycle Bin
To enable the Active Directory Recycle Bin, perform the following steps:
1. Click Start, All Programs, Administrative Tools. Right-click on Active Directory
Module for Windows PowerShell and then click Run As Administrator.
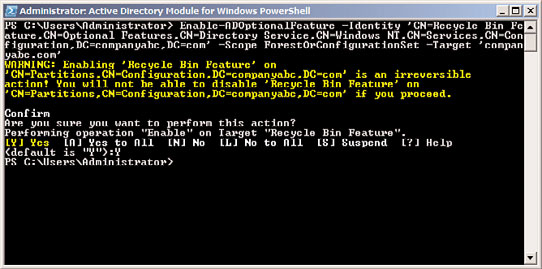
2. From the PowerShell prompt, type the following command, as shown in Figure 4.9.
FIGURE 4.9
Enabling the AD Recycle Bin.
Enable-ADOptionalFeature –Identity ‘CN=Recycle Bin Feature,CN=Optional
Features,CN=Directory Service,CN=Windows
136
CHAPTER 4
Active Directory Domain Services Primer
NT,CN=Services,CN=Configuration,DC=companyabc,DC=com’ –Scope
ForestOrConfigurationSet –Target ‘companyabc.com’
Replace companyabc.com and DC=companyabc,DC=com with the appropriate name
of the domain where the AD Recycle Bin will be enabled.
3. When prompted, type Y to confirm and press Enter.
4. To validate that the Recycle Bin is enabled, go to the CN=Partitions container, using
an editor such as ADSIEdit. In the details pane, find the msDS-EnabledFeature
attribute, and confirm that the value includes the Recycle Bin target domain name
that you typed in step 2.
Recovering Deleted Items Using the AD Recycle Bin
Deleted objects can be restored using the LDP.exe utility, or they can be recovered using
Windows PowerShell. PowerShell offers a much more straightforward approach to recov-
ery of deleted items, and is recommended in most cases.
To recover a deleted object, use the Get-ADObject cmdlet from the Active Directory
Module for Windows PowerShell, being sure to open the module using the Run As
Administrator option. Get-ADObject can be used to find objects, which can then be recov-
ered using the Restore-ADObject cmdlet. For example, the following syntax, shown in
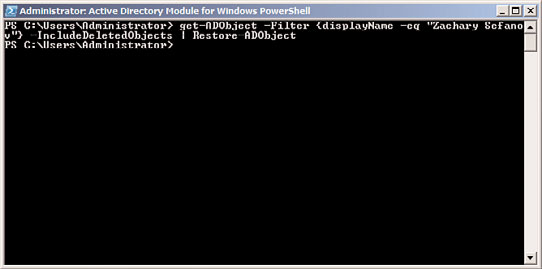
Figure 4.10, recovers a deleted user account for user Zachary Sefanov:
ptg
Get-ADObject –Filter {displayName –eq “Zachary Sefanov”} –IncludeDeletedObjects |
Restore-ADObject
For more information about these cmdlets, type Get-Help Get-AdObject of Get-Help
Restore-ADObject from PowerShell.
Restarting AD DS on a Domain Controller
Windows Server 2008 originally introduced new capabilities to start or stop directory
services running on a domain controller without having to shut it down. This allows
administrators to perform maintenance or recovery on the Active Directory database
without having to reboot into Directory Services Restore Mode.
FIGURE 4.10
Restoring a deleted AD object from the AD Recycle Bin.
Outlining AD DS Changes in Windows Server 2008 R2
137
In addition to allowing for maintenance and recovery, turning off the domain controller
functionality on an AD DC essentially turns that domain controller into a member server,
allowing for a server to be quickly brought out of DC mode if necessary. Microsoft has also
removed the need for local Administrators on the DC to have Domain Admin rights as
well, which improves overall security in places where administration of the DC server is
required, but full Domain Admin rights are not needed.
To take a Windows Server 2008 R2 DC offline, perform the following steps:
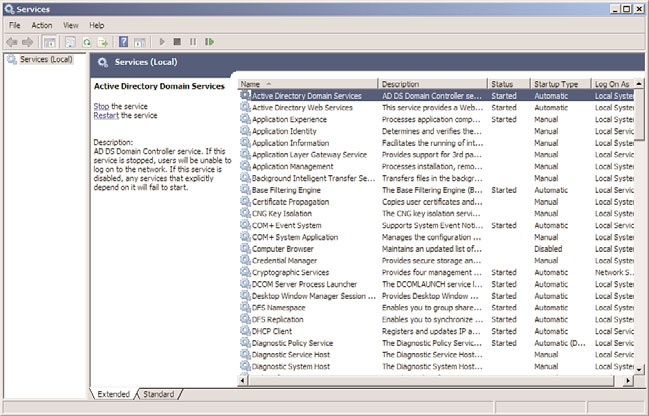
1. Open up the Services MMC (Start, All Programs, Administrative Tools, Services).
2. From the Services MMC, select the Active Directory Domain Services service, as
shown in Figure 4.11. Right-click it and choose Stop.
4
ptg
