Windows Server 2008 R2 Unleashed (162 page)
Read Windows Server 2008 R2 Unleashed Online
Authors: Noel Morimoto

for deployment without any issues. The agents will start automatically and begin to be
monitored as they are discovered.
After installation, it might be necessary to wait a few minutes before the information from
the agents will be sent to the management server.
During the next few minutes after installation, the agent contacts the management server
and establishes a mutually authenticated, encrypted communication channel with the
assigned management server. If the agent was pushed through a software delivery system
such as System Center Configuration Manager 2007 R2, the agent determines the manage-
ment server through Active Directory–integrated discovery.
The agent downloads rules to discover the various applications and components it’s hosting,
allowing the correct application-specific management packs to be applied. This discovery
process runs periodically to ensure the correct rules are always applied to the server.
Configuring Operations Manager 2007 R2
ptg
After installing the Operations Manager 2007 R2 infrastructure, several configuration steps
should be taken to have the system monitor properly, generate Active Directory synthetic
transactions, and send out email notifications of alerts.
Agent Proxy Configuration
Operations Manager 2007 R2 has a variety of security measures built in to the product to
prevent security breaches. One measure in particular is the prevention of impersonation of
one agent by another. That is, an agent SERVER1 cannot insert operations data into the
database about a domain controller DC1. This could constitute a security violation, where
SERVER1 could maliciously generate fraudulent emergencies by making it appear that DC1
was having operational issues.
Although this is normally a good feature, this can be a problem if, in fact, SERVER1 is
monitoring DC1 from a client perspective. The Operations Manager infrastructure would
reject any information presented about DC1 by SERVER1. When this occurs, the system
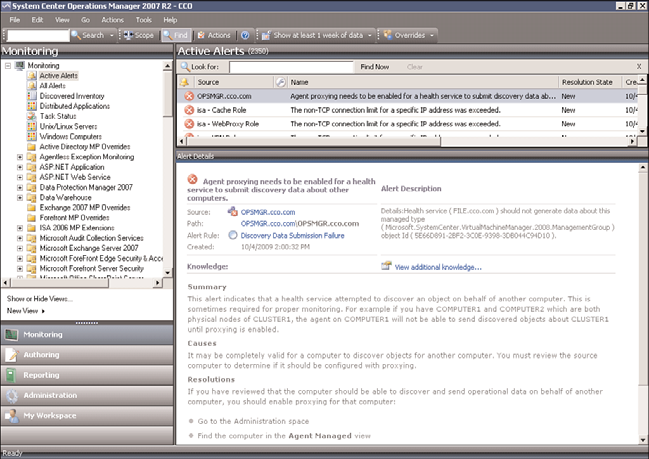
generates an alert to indicate that an attempt to proxy operations data has occurred.
Figure 23.9 shows an example of the alert. In the normal course of events, this alert is not
an indication of an attack but rather a configuration problem.
To get around this problem, Agent Proxy can be selectively enabled for agents that need to
be able to present operational data about other agents. To enable Agent Proxy for a
computer, run the following steps:
1. Open the Operations Manager 2007 R2 console.
2. Select the Administration section.
3. Select the Agent Managed node.
Configuring Operations Manager 2007 R2
823
23
FIGURE 23.9
Agent Proxy alert.
ptg
4. Right-click the agent in the right pane and select Properties.
5. Click the Security tab.
6. Check the Allow This Agent to Act as a Proxy and Discover Managed Objects on
Other Computers check box.
7. Click OK to save.
Repeat this for all agents that need to act as proxy agents.
NOTE
Because the alerts generated by this condition are rule-based and not monitor-based,
the alert needs to be manually resolved by right-clicking on it and selecting Close Alert.
Active Directory Client Monitoring Configuration
Although monitoring performance of Active Directory services is done by the domain
controllers using a variety of measures, sometimes what really matters is how clients
perceive the performance of the domain services. To measure that, the Windows Server
2008 Active Directory management pack can generate synthetic transactions from selected
client systems. These transactions include ADSI bind and search times, LDAP ping and
bind times, global catalog search times, and PDC ping and bind times. The clients execute
tests and log the results, as well as alert on slow performance.
824
CHAPTER 23
Integrating System Center Operations Manager 2007 R2 with
Windows Server 2008 R2
The Active Directory Server Client object discovery is disabled by default. The object
discovery has to be overridden to discover objects that will then run the rules. To selec-
tively override the Active Directory Server Client object discovery, run the following steps:
1. Open the Operations Manager 2007 R2 console.
2. Select the Authoring section.
3. Expand the Management Pack Object node.
4. Select the Object Discoveries node.
5. Select View, Scope.
6. In the Look For field, type Client Perspective. This narrows down the selections.
7. Check the Active Directory Client Perspective target and click OK.
8. Right-click the AD Client Monitoring Discovery and select Overrides, Override the
Object Discovery, and For a Specific Object of Class: Windows Computer.
9. A list of Windows Computer objects will be displayed. Select the computer that will
act as an Active Directory client and click OK.
NOTE
The selected Windows Computer should not be a domain controller.
ptg
10. Check the Override box next to Enabled and set the value to True.
11. In the Select Destination Management Pack pull-down menu, select the appropriate
override management pack. If none exists, create one for the Active Directory
management pack by clicking New.
NOTE
Never use the Default Management Pack for overrides. Always create an override man-
agement pack that corresponds to each imported management pack.
12. Click OK to save the override.
13. Repeat for each Windows computer that will be an Active Directory Server Client
agent.
After a period of time, the selected agents will begin to generate Active Directory client
perspective data and alerts. As a best practice, key Exchange servers are often selected as
Active Directory Server Client agents. It is also a best practice to select at least one agent in
each location to be an Active Directory Server Client agent as well.
Active Directory Replication Monitoring Configuration
The Active Directory management pack can monitor the replication latency between
domain controllers in Active Directory. It uses sources and targets domain controllers,
where the source domain controllers create objects in the OpsMgrLatencyMonitors
Configuring Operations Manager 2007 R2
825
container. These objects are read by the targets, which log performance data in the
OpsMgr databases. There will be a replication counter for each domain partition, for the
DomainDNSZones partition, and for the ForestDNSZones partition between each source
and target pair. There will also be a counter for minimum replication latency and average
replication latency.
The Active Directory management pack has the sources and targets disabled by default
due to the number of counters that can potentially be created. Overrides need to be
created for each source and each target domain controller to get the replication monitor-
ing to function.
23
It is a best practice to reduce the number of sources and targets to a minimum, due to the
number of counters that get created. An example of a source-target model might be to
make all branch offices sources and a single central office DC as the target. Another
example might be to pick a single DC in each site to be in both the source and target
groups, assuming there are a limited number of sites.
The steps to set the source overrides are as follows:
1. Launch the Operations Manager 2007 R2 console.
2. Select the Authoring section.
ptg
3. Expand the Management Pack Objects node.
4. Ensure that the console is not scoped for any objects.
5. Select the Rules node.
6. In the Look For field, enter sources and click Find Now.
7. Select the rule “AD Replication Monitoring Performance Collection (Sources)” in the
“Type: Active Directory Domain Controller Server 2008 Computer Role”.
8. Right-click the rule and select Overrides, Override the Rule, and For a Specific Object
of Class: Active Directory Domain Controller Server 2008 Computer Role.
9. The Select Object window opens and shows matching objects. Select the domain
controller that will be the source and click OK.
10. Check the Override box next to Enabled and set the value to True.
11. In the Select Destination Management Pack pull-down menu, select the appropriate
override management pack. If none exists, create a new management pack named
“Active Directory MP Overrides” by clicking New.
NOTE
Never use the Default Management Pack for overrides. Always create an override man-
agement pack that corresponds to each imported management pack.
12. Click OK to save the override.
13. Repeat for each domain controller that will be a source.
826
CHAPTER 23
Integrating System Center Operations Manager 2007 R2 with
Windows Server 2008 R2
The steps to set the target overrides are as follows:
1. Launch the Operations Manager 2007 R2 console.
2. Select the Authoring section.
3. Expand the Management Pack Objects node.
4. Ensure that the console is not scoped for any objects.
5. Select the Rules node.
6. In the Look For field, enter targets and click Find Now.
7. Select the rule “AD Replication Monitoring Performance Collection (Targets)” in the
“Type: Active Directory Domain Controller Server 2008 Computer Role”.
8. Right-click the rule and select Overrides, Override the Rule, and For a Specific Object
of Class: Active Directory Domain Controller Server 2008 Computer Role.
9. The Select Object window opens and shows matching objects. Select the domain
controller that will be the source and click OK.
10. Check the Override box next to Enabled and set the value to True.
11. In the Select Destination Management Pack pull-down menu, select the appropriate
override management pack. Use the same one from the previous steps when select-
ing the sources.
ptg
12. Click OK to save the override.
13. Repeat for each domain controller that will be a target.
After a period of time, monitoring will begin. Counters will be measuring the replication
latency between the partitions. In addition, replication latency alerts will be triggered if
latency falls below the predefined thresholds.
This sets the sources and targets for Windows Server 2008 domain controllers. For other
versions such as Windows Server 2003 and Windows 2000 Server domain controllers, the
overrides need to be created for those domain controllers separately. Also, the replication
latency mechanism does not support cross-version replication latency measurement.
NOTE
It might be tempting to make all domain controllers both sources and targets. Each
domain controller would then be connected to every other domain controller. This is also
known as a full mesh. However, the problem is that the number of connections grows
as a power of 2. The general function for the number of connection in a full mesh is:
f(x)= (x^2-x)/2
where x is the number of domain controllers and f(x) is the number of connections.
This means that 2 DCs will have 1 connection, 3 DCs will have 3 connections, 4 DCs
will have 6 connections, and so on. By the time you get to 20 domain controllers, you
have 190 connections. The connections are bidirectional and there are at least 5 coun-
ters that are collected per source-target pair, so for 20 DCs in a full mesh, there would
be 1,900 performance counters (190 connections x 2 bidirectional x 5 counters) gath-
ering data. Full mesh is bad!
Configuring Operations Manager 2007 R2
827
Agent Restart Recovery
Agents will heartbeat every 60 seconds by default, contacting their management server to
check for new rules and upload data. On the Root Management Server, there is a Health
Service Watcher corresponding to each managed agent. If the Health Service Watcher for
an agent detects three missed heartbeats in a row (that is, 3 minutes without a heartbeat),
the Health Service Watcher executes a pair of diagnostics:
. First, the Health Service Watcher attempts to ping the agent.
. Second, the Health Service Watcher checks to see if the Health Service is running
23
on the agent.
An alert is then generated for each of the diagnostics if they failed. If the agent is reach-
