Windows Server 2008 R2 Unleashed (164 page)
Read Windows Server 2008 R2 Unleashed Online
Authors: Noel Morimoto

prise CA, the steps need to be completed for the management servers as well.
To request and install the root CA certificate on the DMZ server, execute the following steps:
1. Log on to a DMZ server with local administrator rights.
2. Open a web browser and point it to the certificate server, in this case
https://dc1.companyabc.com/certsrv. Enter credentials if prompted.
3. Click the Download a CA Certificate, Certificate Chain, or CRL link (shown in
Figure 23.10).
4. Click the Download CA Certificate link. Note: If the certificate does not download,
add the site to the Local Intranet list of sites in Internet Explorer.
5. Click Open to open the CA certificate.
6. Click Install Certificate to install the CA certificate.
Monitoring DMZ Servers with Certificates
833
23
FIGURE 23.10
Downloading a root CA certificate.
ptg
7. At the Certificate Import Wizard screen, click Next.
8. Select Place All Certificates in the Following Store option button.
9. Click Browse.
10. Click the Show Physical Stores check box.
11. Expand the Trusted Root Certification Authorities folder and select the local
computer store.
12. Click OK.
13. Click Next, Finish, and OK to install the CA certificate.
14. Close any open windows.
Repeat for all DMZ servers. Now the DMZ servers will trust certificates issued by the certifi-
cation authority. The next step is to request the certificates to use for the mutual authenti-
cation for all servers.
Requesting a Certificate from the Root CA Server
Each of the management servers and the servers in the DMZ will need to be issued certifi-
cates to use for communication.
The steps to request a certificate are as follows:
1. Log on as an administrator, then open a web browser and point it to the certificate
server (in this case, https://dc1.companyabc.com/certsrv).
2. Click the Request a Certificate link.
834
CHAPTER 23
Integrating System Center Operations Manager 2007 R2 with
Windows Server 2008 R2
3. Click the Advanced Certificate Request link.
4. Click the Create and Submit a Request to This CA link.
5. In the Type of Certificate Template field, select Operations Manager.
6. In the Name field, enter the FQDN (fully qualified domain name) of the target server.
NOTE
Go to the actual server to get the name! On the server, go to Computer Properties,
Computer Name. Copy the full computer name and paste it into the Name field of the
form.
7. Click Submit.
8. Click Yes when you get the warning pop-up.
9. Click Install This Certificate.
10. Click Yes when you see the warning pop-up. The certificate is now installed in the
user certificate store.
ptg
NOTE
The certificate was installed in the user certificate store, but needs to be in the local
computer store for Operations Manager. The ability to use web enrollment to directly
place the certificate into the local computer store was removed from the Windows
Server 2008 web enrollment, so the certificate needs to be moved manually.
11. Select Start, Run and then enter mmc to launch an MMC console.
12. Select File and Add/Remove Snap-In.
13. Select Certificates and click the Add button.
14. Select My User Account and click Finish.
15. Select Certificates again and click the Add button.
16. Select Computer Account and click Next.
17. Select the local computer, click Finish, and then click OK.
18. Expand the Certificates – Current User, Personal, and select the Certificates folder.
19. In the right pane, right-click the certificate issued earlier and select All Tasks,
Export. The certificate can be recognized by the certificate template name
Operations Manager.
20. At the Certificate Export Wizard, click Next.
21. Select Yes, Export the Private Key. Click Next.
22. Click Next.
23. Enter in a password and click Next.
Monitoring DMZ Servers with Certificates
835
24. Enter in a directory and filename and click Next.
25. Click Finish to export the certificate. Click OK at the pop-up.
26. Expand the Certificates (Local Computer), Personal, and select the Certificates folder.
NOTE
If this is the first certificate in the local computer store, the Certificates folder will not
exist. Simply select the Personal folder instead and the Certificates folder will be creat-
ed automatically.
23
27. Right-click in the right pane and select All Tasks, Import.
28. At the Certificate Import Wizard, select Next.
29. Click Browse to locate the certificate file saved earlier. Change the file type to
Personal Information Exchange (.pfx) to see the file. Click Next.
30. Enter in the password used earlier, select the Mark This Key as Exportable, and
click Next.
31. Click Next.
ptg
32. Click Finish and then click OK at the pop-up to complete the import.
The preceding steps need to be completed for each DMZ server and for each manage-
ment server.
Installing the Agent on the DMZ Server
The agent needs to be installed manually on each DMZ server. Normally, agents would be
pushed by the Operations Manager console, but DMZ servers typically reside in the DMZ
and are not members of the domain.
The steps to manually install the agent are as follows:
1. Log on as an administrator and insert the OpsMgr 2007 R2 installation media.
2. At the AutoPlay menu, select Run SetupOM.exe.
3. Select Install Operations Manager 2007 R2 Agent from the menu.
4. Click Next.
5. Click Next to accept the default directory.
6. Click Next to specify management group information.
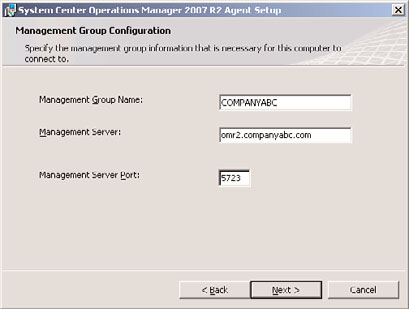
7. Type in the management group name and FQDN of the management server. Keep
the default management server port as 5723. The example shown in Figure 23.11 has
COMPANYABC as the management group name and omr2.companyabc.com as the
management server.
836
CHAPTER 23
Integrating System Center Operations Manager 2007 R2 with
Windows Server 2008 R2
FIGURE 23.11
Manually entered management group information.
8. Click Next.
9. Click Next at the Agent Action Account page to leave the local system as the
action account.
ptg
10. Click Install to complete the installation.
11. When the installer is finished, click Finish.
The preceding steps need to be completed for each DMZ server.
The agent is installed, but will not communicate correctly with the management server.
This is because the agent has not been configured to use the certificate for mutual authen-
tication. This will be done in the next section.
Configuring the Agent to Use the Certificate
After the agent is installed, the agent still needs to be configured to use the correct certifi-
cate. The OpsMgr installation includes a utility called MOMCertImport.exe that configures
the agent to use certificates for authentication and specifies which certificate in the local
computer store to use. The tool does not do any validation checking of the certificate
itself, so care needs to be taken that the correct certificate is selected.
The steps to configure the agent to use a certificate are as follows:
1. Log on as an administrator on the DMZ server and insert the OpsMgr 2007 R2 instal-
lation media.
2. At the AutoPlay menu, select Run SetupOM.exe.
3. Select Browse This CD from the menu.
4. Select the SupportTools directory and then the AMD64 directory.
Using Operations Manager 2007 R2
837
NOTE
Windows Server 2008 R2 is a 64-bit operating system, so the AMD64 is the correct
folder for the 64-bit binaries. If the procedure is being run for 32-bit servers, select the
appropriate directory for the binaries such as i386.
5. In the directory, double-click MOMCertImport.exe.
6. In the pop-up window, select the certificate issued previously and click OK. The
23
View Certificate button can be used to view the certificate details if the correct cer-
tificate is not obvious.
The Operation Manager service will restart automatically to have the certificate selection
take effect. The preceding steps need to be repeated for each DMZ server and for each
management server.
The Operations Manager event log can be viewed with the Windows Event Viewer. It is
named Operations Manager and is located in the Applications and Services Logs folder in
the tool. Any problems with the certificate will be shown in the log immediately follow-
ing the start of the System Center Management service.
ptg
Using Operations Manager 2007 R2
After Operations Manager 2007 R2 has been installed and configured, ongoing work needs
to be done to ensure that the product performs as expected. The two primary activities are
to, first, tune the management packs to ensure that alerts are valid for the environment
and that alert noise is reduced and, second, produce reports of the information that
Operations Manager 2007 R2 is collecting.
Alert Tuning
After deploying Operations Manager 2007 R2, there are frequently complaints about the
number of alert notifications that get generated. This can cause organizations to decom-
mission the product, ignore the emails, or generally complain about what a bad product it
is. In reality, the Operations Manager alert notifications just need to be tuned.
The following process will help you tune the management packs quickly and effectively to
reduce alert and email noise. This is done by adjusting parameters on the rules
(Enable/Disable, Severity, and Priority) using overrides.
Alert Severity is the first parameter to be tuned. There are three levels:
. Critical (2)
. Warning (1)
. Information (0)
838
CHAPTER 23
Integrating System Center Operations Manager 2007 R2 with
Windows Server 2008 R2
The numeric value of the severity is given as well, as some rules and monitors will show
the severity as a value rather than as text.
Alert Priority is the second parameter to be tuned. There are three levels of priority as well:
. High
. Medium
. Low
These tuning procedures assume that the notification subscriptions were created that were
outlined in the “Notifications and Subscriptions” section earlier in the chapter. These noti-
fication subscriptions are as follows:
. Notification for All Critical Severity High-Priority Alerts
. Notification for All Critical Severity Medium-Priority Alerts
When you get an email from an alert that you don’t want, you need to tune the manage-
ment pack monitor or rule. The basic decision tree is as follows:
A. Disable the Alert?
If yes, create an override to disable the rule for either the
instance of the object, the class of objects, or a group of the objects. This prevents
the alert from being generated, so no console alerts and definitely no emails are
ptg
generated. This would be done if the alert does not reflect a real problem.
B. Change Severity?
If yes, create an override to change the alert severity to
Warning. This keeps the alert in the console as a warning, but does not generate an
email. This would be done if the alert is real, but is not actionable.
