Windows Server 2008 R2 Unleashed (256 page)
Read Windows Server 2008 R2 Unleashed Online
Authors: Noel Morimoto

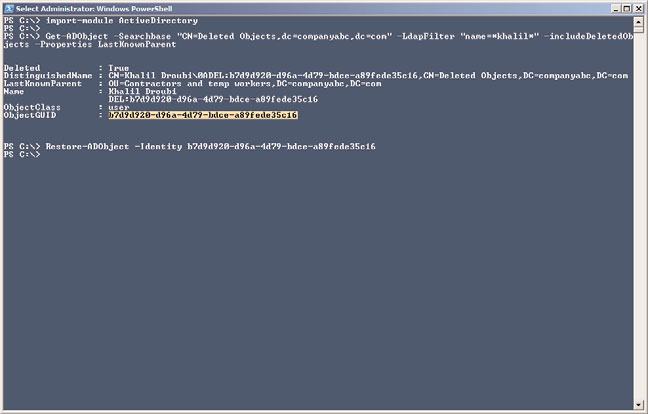
is the case with a default Restore-ADObject command, the parent OU or container
must be present. To determine the parent container of the deleted user object, type
Get-AdObject –Searchbase”CN=Deleted Objects,DC=Company,DC=com” –LdapFilter
“Name=*Khalil*” –IncludeDeletedObjects –Properties LastknownParent and
then press Enter.
1294
CHAPTER 31
Recovering from a Disaster
9. When the LastKnownParent property value is returned, if the value returns a proper
distinguished name, it exists. If the name includes CN=Deleted Objects in the value,
the parent OU or container has also been deleted. If the LastKnownParent has been
deleted, it either needs to be restored before the deleted user object or the user object
needs to be restored to an alternate location using the –TargetPath option in the
Restore-ADObject cmdlet.
10. Assuming that the LastKnownParent value returns an existing container to restore
the object, copy the ObjectGUID of the deleted user account to the Clipboard, type
Restore-ADObject –Identity and paste the ObjectGUID, and press Enter to restore
the object, as shown in Figure 31.8.
ptg
FIGURE 31.8
Restoring a deleted Active Directory user object from the AD Recycle Bin using
the Restore-ADObject cmdlet.
System State Recovery for Domain Controllers
Performing a System State recovery for a domain controller is similar to the recovery of a
member server, but a few more options are presented during the selection process and the
domain controller needs to be booted into Directory Services Restore mode. Recovering
the System State of a domain controller should only be performed if objects were deleted
from Active Directory and need to be restored and the Active Directory Recycle Bin is not
enabled, or if the Active Directory database on the particular domain controller is corrupt
and the Active Directory Domain Services service will not start properly, or if data in the
SYSVOL is missing or corrupted and needs recovery.
Before a domain controller can be booted into DSRM, the DSRM password will be
required. This password is configured when a system is promoted to a domain controller
and is stored locally on each domain controller. The DSRM username is administrator
Recovering Role Services and Features
1295
with no domain designation and the password can manually be changed on a working
domain controller by using the NTDSUTIL utility. To restore the System State of a domain
31
controller, perform the following steps:
1. Log on to the Windows Server 2008 R2 domain controller system with an account
with administrator privileges.
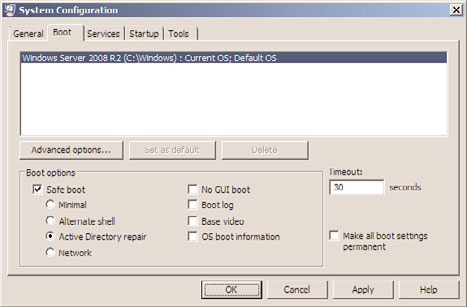
2. Click Start, click All Programs, click Administrative Tools, and select System
Configuration.
3. Select the Boot tab. In the Boot Options section, check the Safe Boot check box, select
the Active Directory Repair option button, as shown in Figure 31.9, and then click OK.
ptg
FIGURE 31.9
Using the System Configuration utility to boot a domain controller into Directory
Services Restore mode.
4. The System Configuration utility will ask for a reboot, and if there are no additional
tasks to perform, click the Restart button to boot the system into DSRM.
5. When the system completes a reboot, log on as administrator with the DSRM pass-
word. Make sure to specify the local server as the logon domain—for example,
server10\administrator instead of companyabc\administrator.
6. Click Start, click All Programs, click Administrative Tools, and select Windows
Server Backup.
7. In the Actions pane, select Recover to start the Recovery Wizard.
8. On the Getting Started page, select This Server (Servername), where
Servername
is
the name of the server to which Windows Server Backup is connected, and click
Next to continue.
9. On the Select Backup Date page, select the correct date and time of the backup you
will use to restore the data, and click Next to continue. Days with a successful
backup are formatted in boldface.
10. On the Select Recovery Type page, select the System State option button, and click
Next to continue.
1296
CHAPTER 31
Recovering from a Disaster
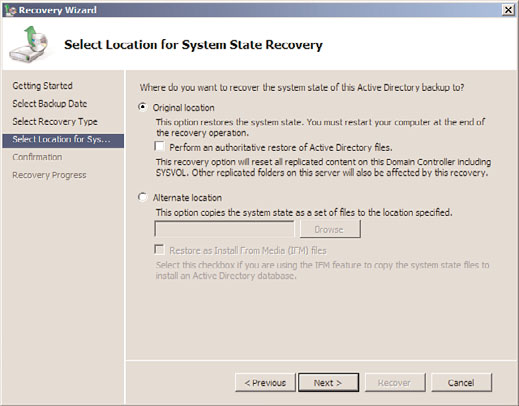
11. On the Select Location for System State Recovery page, select the Original Location
option button. Do not check the Perform an Authoritative Restore of Active
Directory Files check box unless the sysvol folder and content will be marked as the
definitive/authoritative copy and replicated to all other domain controllers. For our
example, we will recover the System State but not mark the SYSVOL as an authorita-
tive restore, as shown in Figure 31.10. Click Next to continue.
ptg
FIGURE 31.10
Restoring a domain controller System State without marking the sysvol data
as authoritative.
12. A dialog box opens that states that this recovery option will cause the server to
resynchronize after recovery; click OK to continue.
13. On the Confirmation page, verify that the System State is listed and that the check
box to automatically reboot the server is not checked. Click Recover to start the
System State recovery of the domain controller.
14. A dialog box opens, detailing that once the recovery is started, it cannot be paused,
and a restart will be required to complete the recovery. Click Yes to start the recov-
ery. System State recovery can take a long time to complete; please be patient.
15. Once the System State restore completes, even if the check box to automatically
reboot is not checked, Windows Server Backup will present a dialog box with a
Restart button and no other option. Restart the server now.
16. Once the server reboots, it will reboot into DSRM again. Log on with the DSRM local
username and password.
17. Once logged in, a wbadmin command prompt opens, stating that the restore
completed successfully. Close the command prompt.
18. Click Start, click All Programs, click Administrative Tools, and select System
Configuration.
Recovering Role Services and Features
1297
19. Select the Boot tab. In the Boot Options section, uncheck the Safe Boot check box
and click OK.
31
20. If an authoritative restore of Active Directory objects is not required, click the Restart
button in the dialog box and allow the server to reboot normally.
21. If an authoritative restore is required, click the Exit Without Restart button in the
dialog box and perform the steps outlined in the “Active Directory Authoritative
Restore” section.
Active Directory Authoritative Restore
When Active Directory has been modified and needs to be restored to a previous state,
and this rollback needs to be replicated to all domain controllers in the domain and possi-
bly the forest, an authoritative restore of Active Directory is required. An authoritative
restore of Active Directory can include the entire Active Directory database, a single
object, or a container, such as an organizational unit including all objects previously
stored within the container. To perform an authoritative restore of Active Directory,
perform the System State restore of a domain controller, but when you are finished, reboot
as directed and when the reboot completes follow these additional steps:
1. Open a command prompt on the domain controller that is running in DSRM and
has just completed a System State recovery and a reboot.
ptg
2. In the Command Prompt window, type NTDSUTIL and press Enter.
3. Type Activate Instance NTDS and press Enter.
4. Type Authoritative Restore and press Enter.
5. To restore a single object, type Restore Object followed by the distinguished name
of the previously deleted object. For example, to restore an object named Khalil
Droubi in the Users container of the companyabc.com domain, type Restore
Object “cn=Khalil Droubi,cn=users,dc=companyabc,dc=com”.
6. To restore a container or organizational unit and all objects beneath it, replace the
“restore object” with “restore subtree” followed by the appropriate distinguished name.
7. After the appropriate command is typed in, press Enter. A window opens, asking for
confirmation of the authoritative restore; click the Yes button to complete the
authoritative restore of the object or subtree.
8. The NTDSUTIL tool displays the name of the text file that may contain any back-
links for objects just restored. Note the name of the file(s) and whether any back-
links were contained in the restored objects.
9. Type quit and press Enter; type quit again to close out of the NTDSUTIL tool.
10. Click the Restart button in the Windows Server Backup dialog box and reboot. Make
sure to set the boot option back to normal boot if not changed previously.
11. After the domain controller reboots into normal boot mode, log on to verify that the
authoritatively restored objects are replicating to the other domain controllers. If
things are working properly, run a full backup of the domain controller and log off.
1298
CHAPTER 31
Recovering from a Disaster
Authoritative Restore Backlinks
When an object is authoritatively restored to Active Directory and if the object was previ-
ously a member of groups in other domains in an Active Directory forest, a file will be
created that defines the restored object backlinks. A backlink is a reference to a cross-
domain group membership. When an object that was previously deleted is authoritatively
restored, the file can be used to update that object’s group membership in the other
domains that contain the groups in question. The NTDSUTIL, upon completion of the
authoritative restore, will list the name of the file that contains the backlink information.
This file can be copied over the domain controller in the different domains and can be
processed by running the command ldifde -i -k -f FileName, where
FileName
repre-
sents the text file created by the NTDSUTIL authoritative restore.
Restoring the Sysvol Folder
When a domain controller System State is restored, the SYSVOL is also restored to the
point in time the backup was taken. If the SYSVOL that has replicated across the domain
needs to be rolled back, an authoritative restore of the SYSVOL, known previously as a
primary restore of SYSVOL, must be performed. To perform an authoritative restore of the
SYSVOL, restore the System State of a domain controller using Windows Server Backup, as
