Windows Server 2008 R2 Unleashed (230 page)
Read Windows Server 2008 R2 Unleashed Online
Authors: Noel Morimoto

ing the Create Now button.
11. After the shadow copies are created, click OK to close the Disk Volume window,
close Server Manager, and log off the server.
For more detailed information concerning the Volume Shadow Copy Service and how to
recover data using previously created volume shadow copies, refer to Chapters 30 and 31.
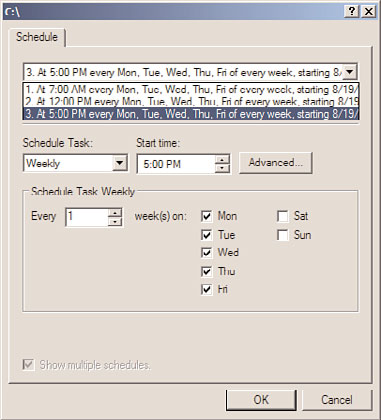
Using the Volume Shadow Copy Service
1169
FIGURE 28.29
Creating an additional schedule for Volume Shadow Copies.
ptg
Recovering Data Using Shadow Copies
The server administrator or a standard user who has been granted permissions can recover
data using previously created shadow copies. The files stored in the shadow copy cannot
be accessed directly, but they can be accessed by connecting the volume that has had a
shadow copy created.
To recover data from a file share, follow these steps:
1. Log on to a Windows Server 2008 R2 system, Windows XP SP1, or later workstation
with either administrator rights or with a user account that has permissions to
28
restore the files from the shadow copy.
2. Click Start and select Run or type in the server and share name in the Search pane.
3. At the Run prompt or Search pane, type \\servername\sharename, where server-
name represents the NetBIOS or fully qualified domain name of the server hosting
the file share. The share must exist on a volume in which a shadow copy has already
been created.
4. When the folder opens, right-click on the folder that contains the data that will be
restored and select Properties.
5. When the window opens, if necessary, select the Previous Versions tab, select the
desired folder version, and click the Open button.
6. An Explorer window then opens, displaying the contents of the folder when the
shadow copy was made. If you want to restore only a single file, locate the file, right-
click it, and select Copy.
1170
CHAPTER 28
File System Management and Fault Tolerance
7. Open the server share location in which the restored file will be placed, right-click,
and choose Paste. Overwrite the file as required and close all the windows as desired.
Windows Server 2008 R2 file services give administrators several options when it comes to
building fault-tolerant servers and data storage as well as fault-tolerant file shares. Through
services such as the Volume Shadow Copy Service, deleted or overwritten files can be
restored automatically or by an administrator without restoring from backup. Using
services such as the Distributed File System and DFS Replication, administrators have more
flexibility when it comes to deploying, securing, and providing high-availability file
services. Using just one or a combination of these file system services, organizations can
truly make their file systems fault tolerant.
The following are best practices from this chapter:
ptg
. Use the Volume Shadow Copy Service to provide file recoverability and data fault
tolerance to minimize the number of times you have to restore from backup.
. Try to provide disk fault tolerance for your operating system and data drives, prefer-
ably using hardware-based RAID sets.
. Do not use a quick format when creating RAID-5 volumes to avoid loss of disk
performance later when data is being first copied to the volumes.
. Use NTFS on all volumes to enable additional file system functionality and security.
. Always define share permissions for every share, regardless of the volume format type.
. Replace the Everyone group with the Domain Users group when shares are created
on domain servers and anonymous or guest access is not required, and set the share
permissions accordingly.
. Use File Server Resource Manager (FSRM) quotas at the folder level instead of NTFS
quotas at the volume for better quota management capabilities.
. Use domain-based DFS roots whenever possible.
. Use DFS to provide a unified namespace to file data.
. Use Window Server 2008 mode on domain-based namespaces to enable access-based
enumeration and improved scalability.
. Start with an empty DFS root folder to keep from having to replicate any data at
the root level and do not create any replication groups based on the namespace
root folder.
Best Practices
1171
. When deploying domain-based DFS namespaces, add additional namespace servers
for redundancy.
. DFS administrators should create and define shares, share permissions, and NTFS
permissions on the shared folder prior to defining these shares as DFS folder targets.
. Replicate DFS data only during off-peak hours to reduce network congestion or
restrict replication with bandwidth constraints if WAN links are heavily used during
business hours.
. When utilizing read-only replicated folders, ensure that replication is only one-way
to the read-only replication folder.
. Back up at least one DFS folder target and configure the backup to not update the
archive bit to avoid possible unnecessary replication.
. Test antivirus programs thoroughly to ensure that no adverse effects are caused by
the scanning of files on a replicated DFS folder target.
. Verify that the drive containing the staging folder for a replication connection con-
tains ample space to accept the amount of replicated data inbound and outbound to
this server.
ptg
28
This page intentionally left blank
ptg
IN THIS CHAPTER
. Building Fault-Tolerant Windows
Server 2008 R2 Systems
. Windows Server 2008 R2
Clustering Technologies
. Determining the Correct
Clustering Technology
. Overview of Failover Clusters
Many businesses today rely heavily on their computer
. Deploying Failover Clusters
and network infrastructure. Internet access, email, instant
. Backing Up and Restoring
messaging, file and print services, and networking services
Failover Clusters
such as domain name system (DNS), Dynamic Host
Configuration Protocol (DHCP), and virtual private
. Deploying Network Load
Balancing Clusters
networking are just a few of the core computer and
networking services that are critical to many businesses. If
. Managing NLB Clusters
one of these critical systems is down or unexpectedly
offline, the impact to the business can be huge. When busi-
ptg
nesses cannot withstand extended periods of unexpected or
unplanned downtime, deploying a fault-tolerant computer
and network infrastructure might be necessary.
Windows Server 2008 R2 provides several methods of
improving system- and service-level fault-tolerance by lever-
aging some of the roles, role services, and features included
in the different editions of the operating system. As an
example, as detailed in Chapter 28, “File System
Management and Fault Tolerance,” the Distributed File
System (DFS) can be used to create and deploy redundant
and automatically synchronized file data through DFS
shares and DFS Replication. Another example of providing
redundant services is to design an infrastructure that
includes multiple domain controllers and print services in
each major site and for remote sites, configuring the Active
Directory site properties to utilize remote site domain
controllers when local services become unavailable.
Windows Server 2008 R2 provides many functions and
services that can extend and enhance the reliability and
resilience of computer and networking services. Many
services, however, are only available when deployed on
specific hardware platforms and when deployed on the
1174
CHAPTER 29
System-Level Fault Tolerance (Clustering/Network Load Balancing)
Enterprise or Datacenter Editions of Windows Server 2008 R2. This chapter covers system-
level fault tolerance using Windows Server 2008 R2 Network Load Balancing (NLB) and
failover clusters. NLB is available in Standard, Enterprise, and Datacenter Editions of
Windows Server 2008 R2. Failover clusters are available only in the Enterprise and
Datacenter Editions of Windows Server 2008 R2. These built-in clustering technologies
provide load-balancing and failover capabilities that can be used to increase fault tolerance
for many different types of applications and network services. Each of these clustering tech-
nologies is different in many ways. Choosing the right Windows Server 2008 R2 clustering
technology depends on the services and applications that will be hosted by the cluster.
Windows Server 2008 R2 technologies such as NLB and failover clusters improve fault
tolerance for services, but before these clustering technologies can be leveraged effectively,
basic server or system stability best practices must be used.
This chapter focuses on the setup and deployment of the Windows Server 2008 R2 cluster-
ing technologies, NLB, and failover clusters, including predeployment checklists to ensure
that the server hardware is more reliable.
Building Fault-Tolerant Windows Server 2008 R2
ptg
Building fault-tolerant Windows Server 2008 R2 systems by utilizing the built-in cluster-
ing technologies consists of carefully planning and configuring server hardware and soft-
ware, planning and configuring the network devices that connect the server to the
network, and providing reliable power for the server. Purchasing high-quality server and
network hardware is a good start to building a fault-tolerant system, but the proper
configuration and selection of this hardware is equally important. Also, providing this
equipment with reliable power and redundant backup power from battery sources and
possibly generators can increase reliability of the servers as well as the networking infra-
structure. Last, but not least, properly tuning the server operating systems to streamline
performance for the desired roles, role services, features, and applications helps enhance
server availability and stability.
Powering the Computer and Network Infrastructure
Powering Windows Server 2008 R2 servers and network hardware with battery or genera-
tor-backed power sources not only provides these devices with conditioned line power by
removing voltage spikes and providing steady line voltage levels, but it also provides alter-
native power when unexpected blackouts or brownouts occur. Many organizations cannot
afford to implement redundant power sources or generators to power the offices, data
centers, and server rooms. For these organizations, the best approach to providing reliable
power to the computer and network infrastructure is to deploy uninterruptible power
supplies (UPSs) with battery-backed power. With a UPS, power is normally supplied from
the batteries, which are continually charged by the utility line power. When the line
power fails, a properly sized UPS provides ample time for end users to save their data to
the server and to gracefully shut down the server or network device without risk of
damaging hardware or corrupting data.
Building Fault-Tolerant Windows Server 2008 R2 Systems
1175
UPS manufacturers commonly provide software that can send network notifications, run
scripts, or even gracefully shut down servers automatically when power thresholds are
reached. Of course, if end-user data is important, each end-user workstation and the
network switches that connect these workstations to the computer and network infrastruc-
ture should also be protected with UPSs that can provide at least 5 to 10 minutes of
battery-backup power.
One final word on power is that most computer and network hardware manufacturers
offer device configurations that incorporate redundant power supplies designed to keep
the system powered up in the event of a single power supply failure.
Designing Fault-Tolerant IP Networks
Network design can also incorporate fault tolerance by creating redundant network routes
and by utilizing technologies that can group devices together for the purposes of load
