Windows Server 2008 R2 Unleashed (202 page)
Read Windows Server 2008 R2 Unleashed Online
Authors: Noel Morimoto

update installation and remote management options.
Creating Local Administrators and Non-Administrators Policies
ptg
When a Windows system is first deployed, only the local computer group policy is
created. Local group policies for administrators, nonadministrators, and individual local
users need to be manually created if they are to be utilized. The process of creating the
Administrators or Non-Administrators policy must be performed from the local machine
using the Group Policy Object Editor. In the following example, create a local group policy
for the Administrators group. To create a local user group policy for administrators,
perform the following steps:
1. Log on to the Windows Server 2008 R2 system with an account with administrator
privileges.
2. Click Start, click in the Search pane, type MMC, and press Enter.
3. When the Microsoft Management Console opens, click File from the menu bar, and
select Add/Remove Snap-In.
4. In the Add or Remove Snap-Ins window, in the Available Snap-Ins pane on the left,
scroll down and select the Group Policy Object Editor, and click the Add button.
5. The Select Group Policy Object window opens and defaults to the local computer
policy. Click the Browse button to choose a different policy.
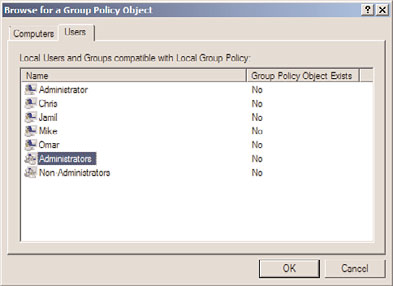
6. In the Browse for a Group Policy Object window, select the Users tab.
7. On the Users tab, each local user account will be listed as well as Administrators and
Non-Administrators. Select Administrators and click OK, as shown in Figure 27.1.
Planning Workgroup and Standalone Local Group Policy Configuration
1035
FIGURE 27.1
Selecting the local group policy for administrators.
8. Back in the Select Group Policy Object window, the Group Policy Object name
should reflect Local Computer\Administrators. If the name matches, click Finish to
return to the Add or Remove Snap-Ins window.
9. In the Add or Remove Snap-Ins window, click OK to complete adding snap-ins to
this console window.
ptg
10. In the MMC window, the Local Computer\Administrators policy will be available for
editing. Because this policy only applies to users in the Administrators group, only
the User Configuration node is present.
11. Configure at least one setting in this policy to create it and close the MMC window
when the configuration of the local user group policy for administrators is complete.
27
12. When prompted to save the console, click No and log off of the server.
13. Log back on to the server with an account with local Administrator rights.
14. Click Start, click in the Search pane, type cmd, and press Enter.
15. Type gpresult /h LGPO-Administrators.html and press Enter. The gpresult
command with the /h option generates an HTML file that will be used to determine
if the local user group policy for administrators has been applied. This option is only
available on Windows Vista, Windows 7, Windows Server 2008, and Windows Server
2008 R2 systems, but the tool can be run against remote systems with the proper
permissions and firewall settings configured.
16. After gpresult completes, in the command prompt type the name of the file
created, in this example LGPO-Administrators.html, and press Enter.
17. The previous command will launch Internet Explorer; notice that the browser might
require permission to allow the Active X content to load.
18. After allowing the Active X content and functionality, scroll down to the User
Configuration Summary section and click on the Group Policy Objects link.
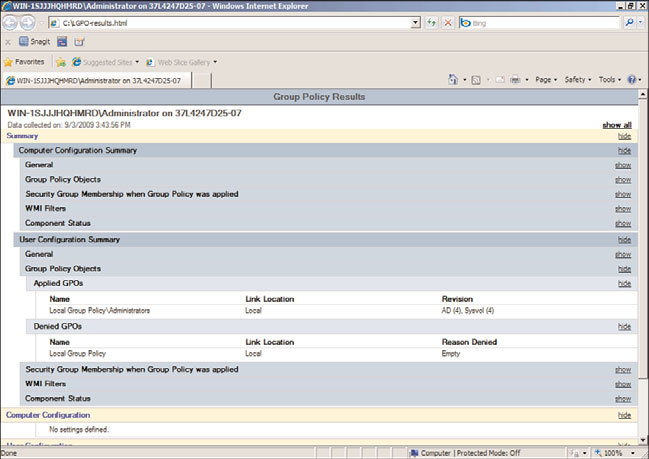
19. Click on Applied GPOs and Denied GPOs to reveal which policies were applied to
the user, as shown in Figure 27.2.
1036
CHAPTER 27
Group Policy Management for Network Clients
FIGURE 27.2
Verifying GPO application using the gpresult HTML report.
ptg
20. Review the HTML report and when finished, close Internet Explorer and log off.
The same procedure can be used to create local group policies for nonadministrators or
individual local user accounts.
Planning Domain Group Policy Objects
Group Policy Objects (GPOs) can be used to perform many functions across a diverse or
standard computer and network infrastructure built on Microsoft Windows and Active
Directory Domain Services. Considering how to best utilize group policies to manage any
one particular environment and deciding on which GPO settings to leverage can be a
lengthy process. To simplify this process and to keep from rethinking GPO usage each
time, a base set of GPOs should be created and stored as starter GPOs.
A starter GPO is a feature of the Group Policy infrastructure that first became available
with the release of the Windows Server 2008 Group Policy Management Console. A starter
GPO can contain a set of Group Policy administrative template settings that have been
preconfigured or defined to meet an organization’s security and/or configuration require-
ments. When a new GPO is created, a starter GPO can be leveraged to prepopulate the
defined settings into the new GPO. The benefit is that each time a GPO is needed, it does
not have to be created from scratch and the administrator does not need to search for
each of the settings that are necessary to meet the specific object of the new GPO.
Windows Server 2008 R2 provides several starter GPOs for Windows XP and Windows
Vista systems that have been created to provide preconfigured security settings to meet
Planning Domain Group Policy Objects
1037
the best-practice recommendations outlined in the Windows Vista and Windows XP secu-
rity guides. For more information on starter GPOs, refer to Chapter 19. The remainder of
this section outlines common scenarios for GPO usage to assist administrators with the
planning, deployment, and configuration of GPOs across an organization’s Active
Directory infrastructure.
Policies and Preferences
Windows 2008 Group Policy introduced a brand-new set of configurable settings known
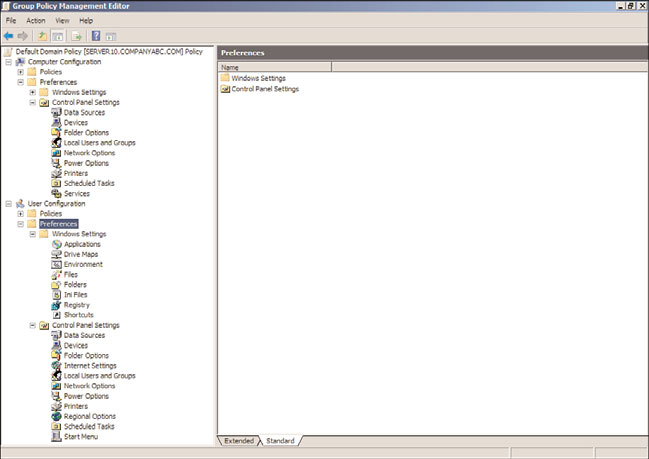
as Preferences. Group Policy Objects are now organized into Policy settings and Preference
settings, as shown in Figure 27.3. Preferences provide many of the features that the Group
Policy infrastructure was lacking in previous versions, and preferences also provide many
functions that were commonly handled with complex logon and startup scripts, with
Registry file import tasks, and by administrators configuring the default user profile on
workstations and servers. Many preference settings, such as Registry keys and Drive Maps,
would have previously been applied with scripts that required the workstation to be
logged on to or started up on the internal network. With preference settings in domain
group policies, these settings can now be applied during the Group Policy refresh interval,
which can greatly increase the successful application of these types of settings.
ptg
27
FIGURE 27.3
Group Policy User Configuration Preferences.
Policy settings and Preference settings have different characteristics. Policy settings are
enforced and all users are commonly restricted from changing any configured policy
setting. If a policy setting contains a graphic interface, when configured, the setting is
normally grayed out to the end user, as shown in Figure 27.4 for the policy-configured
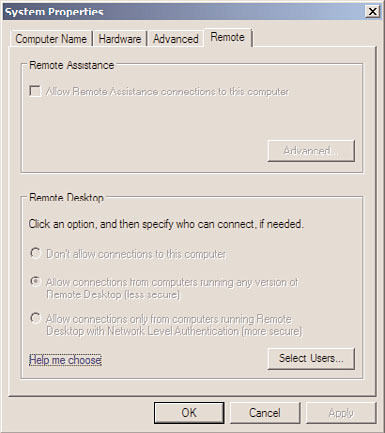
1038
CHAPTER 27
Group Policy Management for Network Clients
Remote Desktop settings. Policy settings such as software installations and computer or
user scripts are only processed during computer startup or shutdown and user logon and
logoff cycles.
ptg
FIGURE 27.4
Enforced Remote Desktop policy setting.
Preference settings are applied to computers and users the same as policy settings: during
startup, shutdown, and refresh cycles for computers and logon, logoff, and refresh cycles
for users. Preferences settings, however, are configured but not enforced. As an example of
this, using a user printer preference, a printer can be installed in a user profile and set to
be the default printer but the end user will still retain the ability to define a different
default printer if necessary. Preference settings are applied during refresh intervals, but
certain settings, such as creating Registry keys and values, might require a computer
reboot or user logoff/logon cycle to actually apply the new setting. One important point
to note is that the domain group policy preferences are supported on Windows 7,
Windows Server 2008, and Windows Server 2008 R2, but Windows XP, Windows Server
2003, and Windows Vista all need an update to support preference settings.
Preference settings are all different, but they each share common administrative function-
ality. Each preference setting will either be presented in a graphic interface similar to, if
not exactly, what the end user can see and access within the user profile. This is one
distinction between preference and policy settings, as most policy settings are enabled,
disabled, or not configured whereas a preference setting can contain several configuration
features. Furthermore, each preference settings can have multiple items defined within it,
each with a separate configuration value. As an example, a Drive Map preference can have
a setting item of a mapped drive P and a mapped drive U defined within the single
domain group policy preference setting.
Planning Domain Group Policy Objects
1039
In addition to the specific setting options that are unique to each preference, such as the
drive letter designation for a Drive Map or a folder path to a Network Share preference, each
