Windows Server 2008 R2 Unleashed (203 page)
Read Windows Server 2008 R2 Unleashed Online
Authors: Noel Morimoto

setting also contains a set of common options and many also include a preference action.
Preference Actions
Preference actions determine how a preference setting will be applied to a user or computer.
Many preference settings also contain an option called the preference action. The most
common preference actions include the Create, Replace, Update, and Delete actions:
.
Create—
The Create action creates or configures the preference setting if the setting
does not already exist. If the setting already exists, no action is taken.
.
Replace—
The Replace action deletes and recreates the setting on the computer or
within the user profile.
.
Update—
The Update action creates the setting if it does not exist, but if the setting
already exists, part or all of the setting configurations are updated to match the pref-
erence setting. Update is the default action and is less intrusive than the Replace
action. It can be used to ensure that the setting is configured as desired, but process-
ing speed will be optimized because if the setting already matches it will be skipped.
.
Delete—
The Delete action simply deletes the preference setting from the computer
ptg
or user profile. For example, a Delete action can remove a mapped drive, delete a
Registry key, or delete a printer from a computer or a user profile.
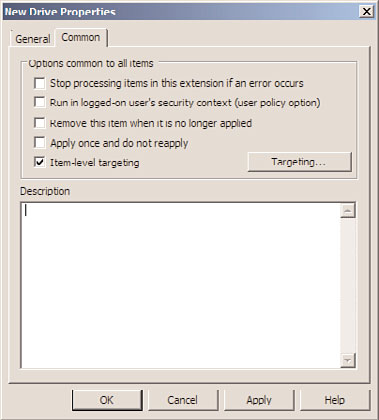
Preference Common Options
Each preference setting contains a common tab that contains several options that can be
27
enabled for the particular setting. A list of the common options is shown in Figure 27.5.
Common options include the ability to process the setting only once, which is great for
setting default configurations for new user profiles or a new preference setting on existing
domain group policies.
Item-Level Targeting
One of the most functional preference common options is the item-level targeting option.
Item-level targeting allows administrators to define the scope of application for a particu-
lar preference setting item such as a Drive Map. So with item-level targeting an adminis-
trator can create a single domain group policy and have a single Drive Map preference
defined that will apply different preference setting items to subsets of computers or users
based on the specifications of the item-level target. For example, a Drive Map preference
that defined the G drive for groups can be configured to map \\server10\Sales to
members of the domain security group named sales, based on the item-level targeting
option configuration settings. The same preference can also define the G drive to
\\server10\HR for members of the domain Human Resources group based on a different
configuration for item-level targeting.
1040
CHAPTER 27
Group Policy Management for Network Clients
FIGURE 27.5
Group policy preference common options.
ptg
Domain GPOs
When an Active Directory domain is deployed, a default domain policy and a default
domain controller policy are created. The default domain policy defines the password and
account policies for all domain user accounts and local user accounts for domain member
servers and workstations. A few additional settings are also defined within the default
domain policy regarding the Encrypting File System, Kerberos authentication, and a few
other network-related security settings.
As a best practice, the only changes that should be made to the default domain policy
should be modifying the password and account policy settings and nothing else.
Additional settings that are required at the domain level should be defined in separate
policies linked to the domain. The settings configured on domain-linked GPOs will be
applied to all computer and user accounts in the domain, including all domain
controllers. Settings configured at the domain level should be deployed as default settings
and not as organizational standards. For example, as a domain default, the organization
might want to configure all computers to enable Windows Update and get updates from
the Windows Software Update Services (WSUS) at headquarters and to configure a few
default firewall exceptions to allow for remote administration from the IT department.
Common default settings applied at the domain level, but not in the default domain
policy, can include the following:
. Default screensaver settings
. Default Windows Update settings
. Default firewall profile and rule configurations
. Default Encrypting File System settings and recovery agent
Planning Domain Group Policy Objects
1041
. Trusted root certification authorities
. Certificate enrollment configurations
All Windows systems that are members of an Active Directory domain will inherit the user
password and account policies from the domain and apply this policy to local accounts on
these systems. In some cases, it might be necessary to leverage local user accounts on
systems with a less-restrictive password policy to support a particular service or applica-
tion. This task can be accomplished by adding a GPO at the organizational unit that
defines a less-restrictive password and account lockout policy. This particular password
and account lockout policy will only apply to local user accounts on the computers
contained within the linked organizational unit. The only thing that will break this
configuration is if the default domain policy is enforced. For more information on domain
policy enforcement, refer to Chapter 19.
In situations when special or specific domain user accounts cannot adhere to the domain
password policy, if the domain is operating in Windows Server 2008 or Windows Server
2008 R2 domain functional level, a fine-grained password policy can be created and applied
to the necessary user accounts. Fine-grained password policies are new to Active Directory
and are detailed later in this chapter in the section “Fine-Grained Password Policies.”
ptg
Domain Controller GPOs
When an Active Directory domain is deployed, a default domain controller policy is
created. This is different from the default domain policy in many ways, but the most
prevalent distinction is that this policy is applied to the domain controllers organizational
unit and not the entire domain. The default domain controller policy only applies to
objects in this organizational unit, which should contain all of domain controllers of the
27
specific domain, and no other objects.
The domain controllers organizational unit inherits all policies linked to the domain and
each domain controller also inherits any site-linked GPOs if any exist. These policies will
be applied by the domain controllers and might not be desirable. As a best practice, to
avoid impacting domain controller security and reliability, try to limit the configuration
settings defined within domain-linked policies or specifically deny the application of these
group policies to the enterprise domain controllers security group within each domain of
the forest.
NOTE
Moving a domain controller out of the domain controllers organizational unit is not rec-
ommended as adverse effects could result, including compromising the security of the
entire domain as well as breaking authentication and replication functionality.
The default domain controller policy defines user rights assignment settings for domain
controller management as well as defines settings to control the security of network
communication. Most organizations do not require any changes made to the default
1042
CHAPTER 27
Group Policy Management for Network Clients
domain controller policy or any additional policies linked to the domain controllers orga-
nizational unit. Common settings applied at the domain controller organizational unit
level can include the following:
. User rights assignment updates for domain controllers (commonly used for backup
agent accounts)
. Restricted group policies for domain security groups
. Event Viewer settings
. Audit settings for domain controllers
. Domain controller–specific Windows Update settings
. Remote administration settings for domain controllers
Active Directory Site GPOs
By default, no group policies are created for Active Directory sites. Policies linked to Active
Directory sites will be applied to all computers that connect to the domain from the
particular subnets associated with the site and, of course, the users who log on to these
particular computers. If computers are moved to new sites, these computers will pick up
and process any policies linked to the new site and none from the original site. For
ptg
example, if an Active Directory site is created for the virtual private network (VPN), when
a computer is connected to the corporate network using the VPN, any policies linked to
the VPN site will be applied to the computer.
Site policies can be a very effective way to simplify administration of mobile users, but if
used incorrectly, site policies can cause a lot of issues. For example, using site policies to
deploy printers can simplify end-user management for visiting employees. On the other
hand, installing software for all computers in a site or enforcing networking settings might
impact mobile computers if these settings are not overwritten or restored when the user
and the system return back to the main office or disconnect from the corporate network.
Site GPOs are not commonly used, but when they are, some of the common settings can
include the following:
. Wireless and Wired Network Policies
. Deployed Printers (User Configuration)
. Internet Explorer Proxy Configuration
Small Business
Many small businesses run Windows Server systems and Active Directory domains. Unless
these businesses run an edition of Small Business Server, most small business Active
Directory infrastructures do not effectively leverage local or domain group policies using
the default configuration. Many of these Active Directory deployments are flat and all
computers and users remain in the default containers and only apply the default domain
policy. For small businesses with limited IT resources and budget, aside from updating the
password and account lockout settings in the default domain policy, there are a few GPO
Planning Domain Group Policy Objects
1043
settings that can enhance management and reliability. Please keep in mind that the
following small business group policies are not recommended for Small Business Server
(SBS) or Essential Business Server (EBS) deployments, as SBS and EBS deploy a number of
preconfigured policies that provide some of the features included in the following policies
and much more.
Group Policy management for small businesses should be kept simple. The following list
of recommendations should be considered for small business Group Policy configurations:
1. Review and, if necessary, adjust the password and account lockout policy in the
default domain policy to match the requirements of the organization.
2. Create a new policy named Corporate Computer Policy and disable the User
Configuration section of this policy. Within this policy, configure Windows Update
settings, deploy network printers, enable remote administration, and configure fire-
wall exceptions or rules to allow for proper communication between the servers and
workstations on the network. If necessary, also configure Internet Explorer Security
Zone settings. Link this policy to the domain.
3. Create a new policy named Corporate User Policy and disable the Computer
Configuration section of this policy. Within this policy, configure user mapped
drives, default screensaver settings, and, if necessary, lock down the desktop, Start
menu, and Control Panel. In some cases, folder redirection configuration would also
ptg
be recommended, but this is an advanced configuration and might not be feasible
for small businesses. Link this policy to the domain.
4. Edit the default domain controller policy and configure the Windows Update set-
tings to download and notify the administrator when updates are ready. Many orga-
nizations configure Windows Update on workstations to autoinstall and autoreboot,
